Microsoft recently announced its release of Azure AD Connect 2.0 and today we’re going to upgrade our lab from 1.4.18.0 to 2.0.10.0. If you’ve never installed Azure AD Connect, check out our video to install it from scratch. In our case, since we’re using a local database, we’re going to upgrade. Another option you could consider is doing a swing migration so you don’t have to touch your original setup.
Per Microsoft, several of the older components that Azure AD Connect uses have been scheduled for deprecation. To mitigate the issue, they bundled as many of these newer components into a single release so you only have to update once.
So What Are the Major Changes in Azure AD Connect 2.0
If you recall, the previous version of AAD Connect shipped with SQL Server 2012. Seeing as how SQL 2012 will be out of extended support in 2022, they’ve decided to bundle SQL Server 2019 when you install it.
Another major note to take in account is the new version of AAD Connect will now have Microsoft Authentication Library (MSAL), where as the previous version had Active Directory Authentication Library (ADAL) installed. MSAL uses Microsoft Graph Endpoints on the backend to make sync processes much faster.
Next up is Server 2012 and Server 2012 R2 are no longer supported for AD Connect and with that is a requirement to have PowerShell 5.0 installed on the machine. The good thing is that Server 2016 and Server 2019 have Powershell 5.0 installed by default.
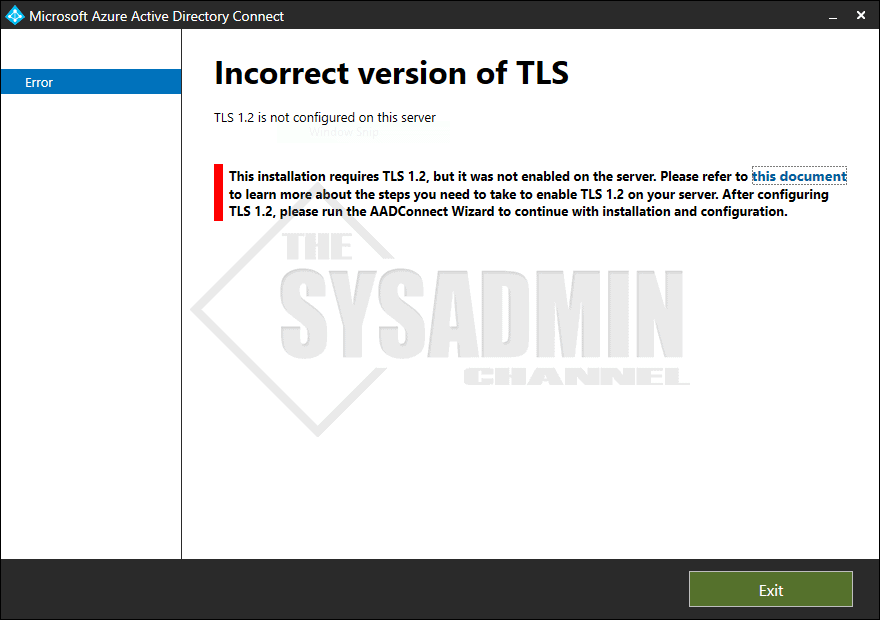
Furthermore, if you have tried to install AAD Connect v2.0 and you’re not on Server 2019 you might have noticed that you’re immediately prompted with a warning of an incorrect TLS version. If you’re doing your homework before installing the new version, just know that TLS 1.0 and TLS 1.1 are protocols that are being deprecated by Microsoft because they are now deemed unsafe. This release of Azure AD Connect will only support TLS 1.2. If your server does not support TLS 1.2 you will need to enable this before you can deploy Azure AD Connect v2.0.
Enable TLS 1.2 For Azure AD Connect v2.0
Straight out of their documentation, Microsoft has already posted the Powershell script to enable TLS 1.2. Here is the exact replica so you don’t have to go to another place. Make sure you Powershell as an Administrator because you will change the state of the machine.
New-Item 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null Write-Host 'TLS 1.2 has been enabled.'
Once that is ran, go ahead and reboot the server to make sure you install AAD Connect on a fresh system.
Upgrade To Azure AD Connect 2.0 Step by Step
First things first, you’ll need to download the latest version on Microsoft’s website here.
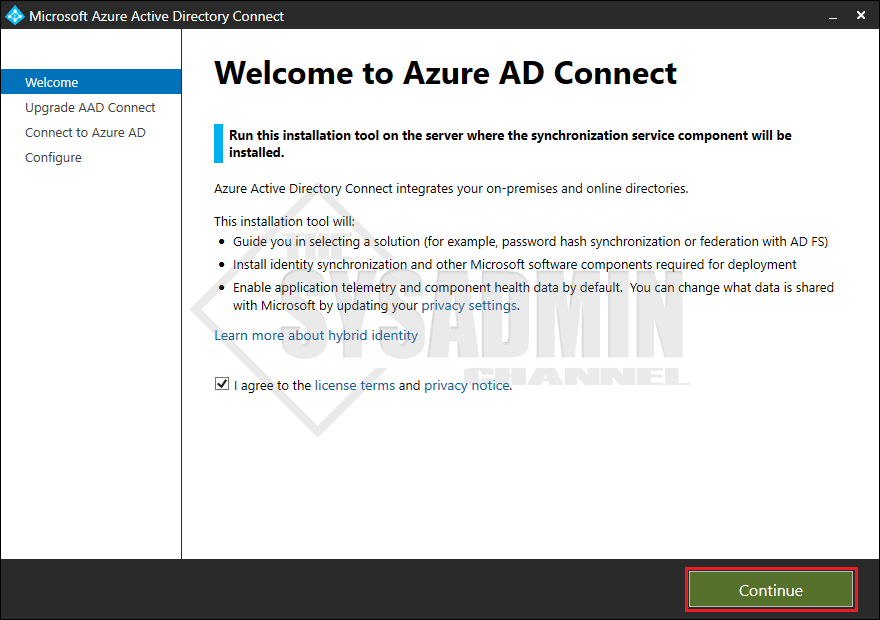
- After the initial MSI is ran and the setup is completed, you’ll be prompted with the welcome screen
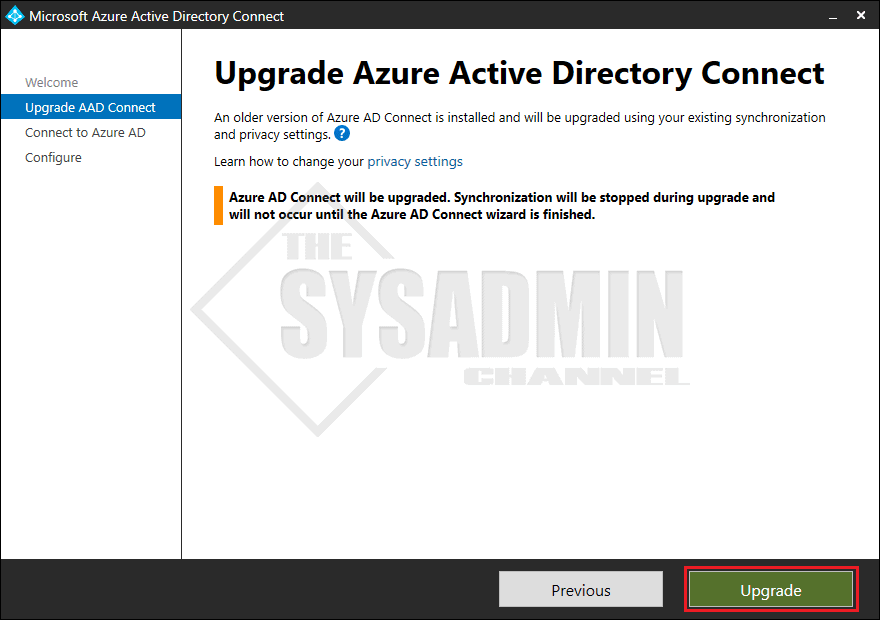
- Select Upgrade when you reach this prompt
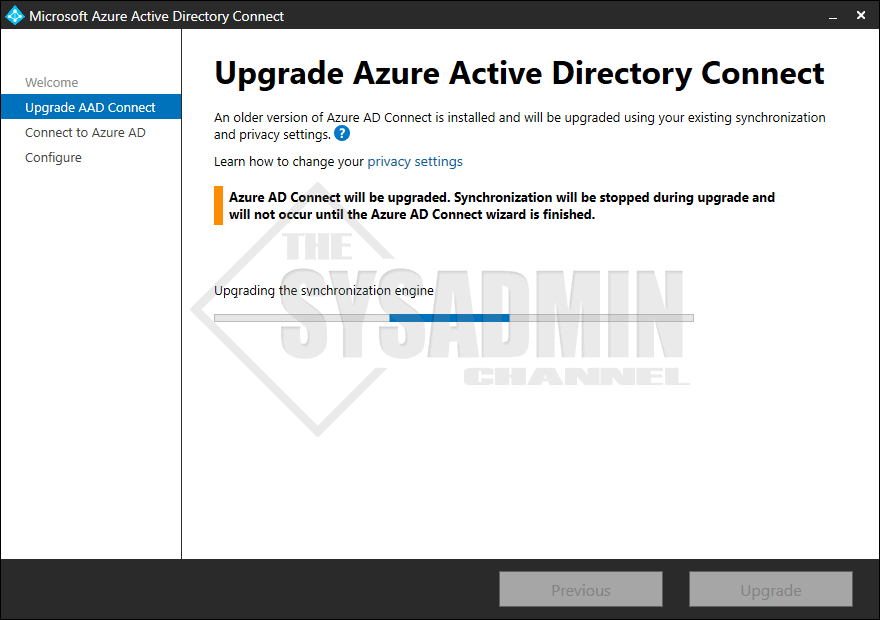
- Azure Active Directory Connect will now upgrade the Sync Engine
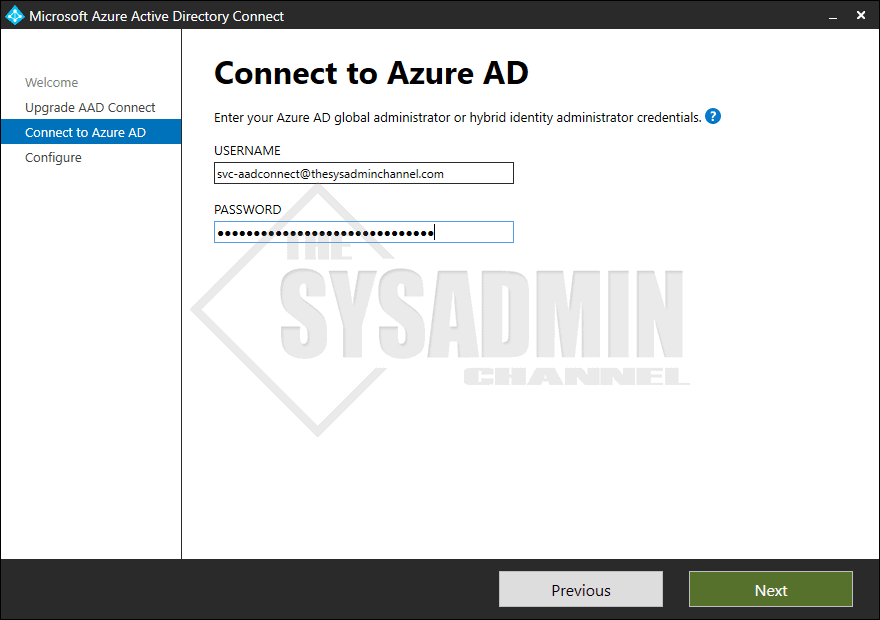
- Once the Sync Engine is upgraded, you will be prompted to enter in credentials
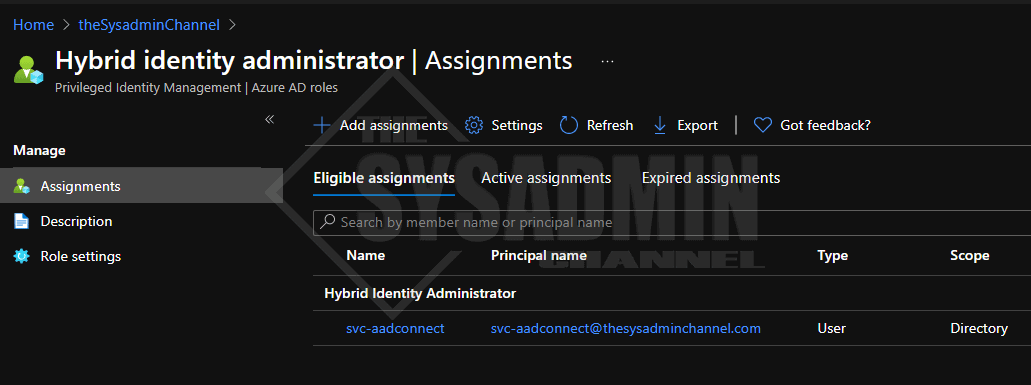
- AAD Connect no longer needs a Global Administrator to upgrade, you can now use a Hybrid Identity Administrator
- Following the least privilege model, we’ll enter in a Hybrid Identity Administrator account that also needs to be activated with PIM
- To continue the installation, enter a Global Administrator -or Hybrid Identity Administrator account (we’ll activate our hybrid identity role)
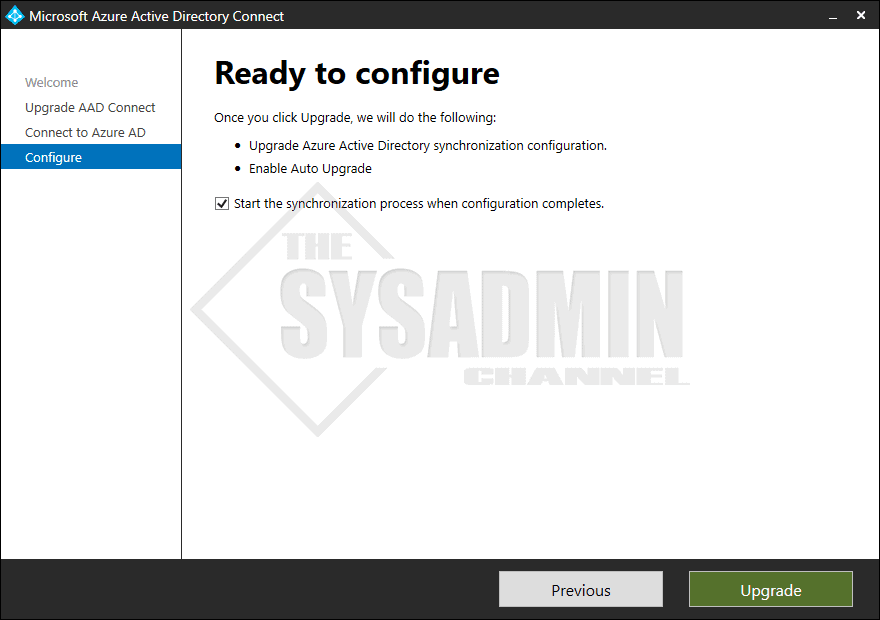
- Once Azure has confirmed the credentials, select Upgrade to start the sync process.
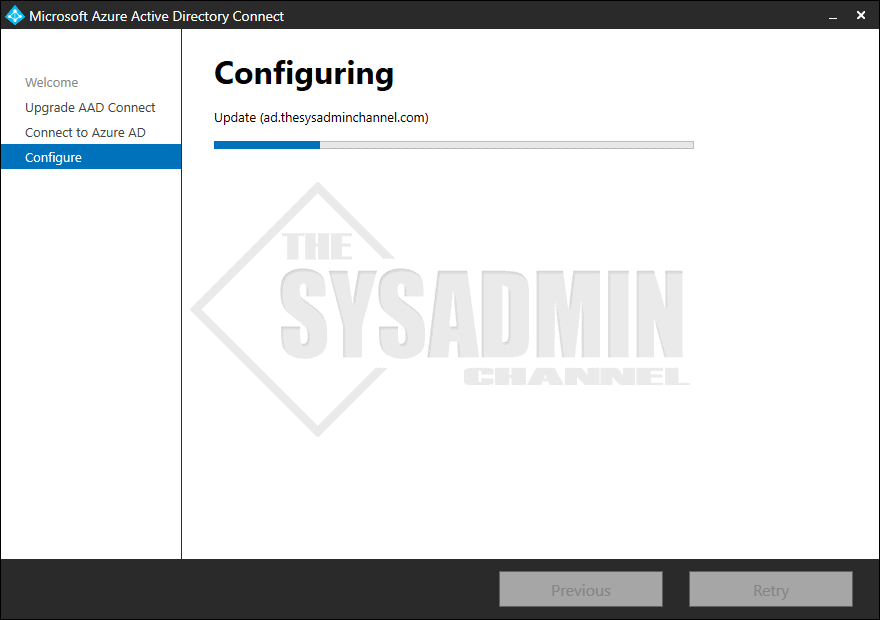
- The setup will now run several update processes
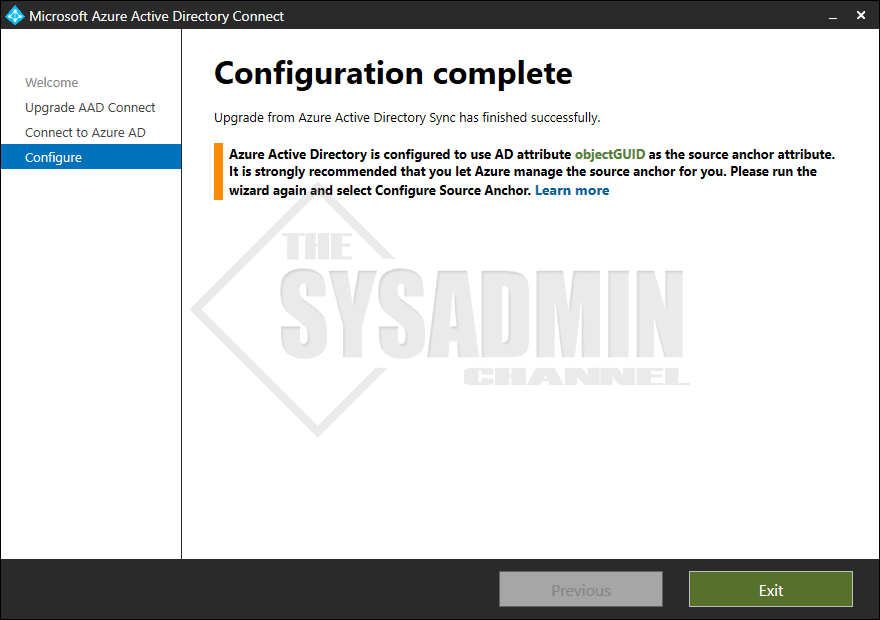
- If everything was successful, you should see Configuration Complete
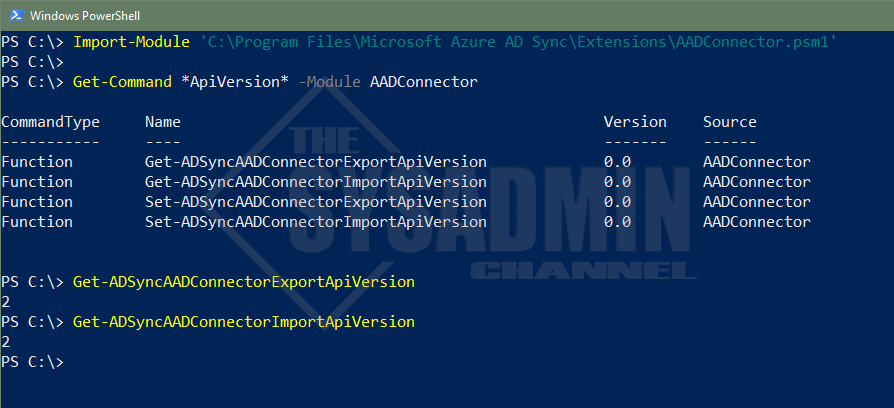
- Last but not least, open the Synchronization Service Manager -> Help -> About
- You should be able to confirm the version is now above. 2.0
- You should also be able to confirm you’re using AD Connect v2 EndPoint API
PS C:\> Import-Module 'C:\Program Files\Microsoft Azure AD Sync\Extensions\AADConnector.psm1' PS C:\> PS C:\> Get-Command *ApiVersion* -Module AADConnector CommandType Name Version Source ----------- ---- ------- ------ Function Get-ADSyncAADConnectorExportApiVersion 0.0 AADConnector Function Get-ADSyncAADConnectorImportApiVersion 0.0 AADConnector Function Set-ADSyncAADConnectorExportApiVersion 0.0 AADConnector Function Set-ADSyncAADConnectorImportApiVersion 0.0 AADConnector PS C:\> Get-ADSyncAADConnectorExportApiVersion 2 PS C:\> Get-ADSyncAADConnectorImportApiVersion 2 PS C:\>
Conclusion
Well hopefully this article was able to help you upgrade to Azure AD Connect 2.0. It’s actually not that bad of an install and it’s not too involved so hopefully you won’t run into any issues if/when you decide to upgrade it in your environment.
One thing I forgot to mention is that if you have specific rules on your AD Connect Server, those will need to confirmed so it doesn’t cause any impact.



Hi,
I’m having problem upgrading from 2.1.1.0 to 2.1.15.0 with same “index out of range error”. Any ideas ?
Tks
Will this install work on Server 2012 r2?
Or are you saying that the AADconnect v2 upgrade will include upgrade to sql 2019 and will be upgraded also??
This will not work on Server 2012 so you will need to setup on a new 2019 server and do a fresh install. Anything 2012 will not be supported.
hello thanks for this tuto , i have ad connect installed on windows server 2012 R2
since old components no longer supported by MS , do i have to create new server 2019 to install adconnect V2 ? or just lanch the upgrade in place in the same server and enabled TLS1.2
Thank u
I would recommend setting up a new 2019 server and installing from scratch. This new setup should be setup in staging mode and you migrate when you’re ready.