If you’ve recently deployed MFA (Multi-Factor Authentication) in Office365/ Azure you may find that there is no easy way to report who has MFA enabled, and more importantly, which of your administrators don’t have MFA enabled. I ran across a problem that I needed to solve so I turned to Powershell for my solution. Therefore, I created a script to get MFA status using Powershell.
Here we will assume you have the correct permissions to access the MSOL service and the email address and userprincipalname are the same
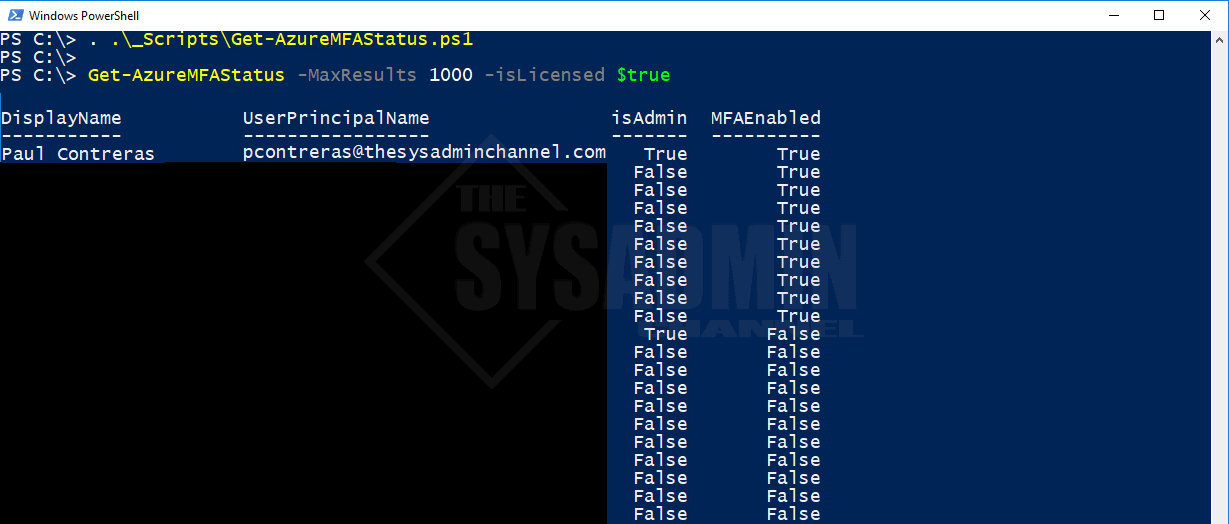
Get MFA Status Using Powershell
Function Get-AzureMFAStatus {
<#
.Synopsis
This will get the Multi-factor authentication status of your users and determine which of them or not are admins.
For updated help and examples refer to -Online version.
.DESCRIPTION
This will get the Multi-factor authentication status of your users and determine which of them or not are admins.
For updated help and examples refer to -Online version.
.NOTES
Name: Get-AzureMFAStatus
Author: theSysadminChannel
Version: 1.0
DateCreated: 2019-Feb-08
.LINK
https://thesysadminchannel.com/get-mfa-status-for-azure-office365-users-using-powershell -
#>
[CmdletBinding(DefaultParameterSetName="Default")]
param(
[Parameter(
Position = 0,
Mandatory = $false,
ValueFromPipeline =$true,
ValueFromPipelineByPropertyName=$true,
ParameterSetName = "UserPrincipalName"
)]
[string[]] $UserPrincipalName,
[Parameter(
Mandatory = $false,
ValueFromPipeline = $false,
ParameterSetName = "ResultList"
)]
[int] $MaxResults = 2000,
[Parameter(
Mandatory = $false,
ValueFromPipeline = $false,
ParameterSetName = "ResultList"
)]
[bool] $isLicensed = $true,
[Parameter(
Mandatory = $false,
ValueFromPipeline = $false
)]
[switch] $SkipAdminCheck
)
BEGIN {
if (-not $SkipAdminCheck) {
$AdminUsers = Get-MsolRole -ErrorAction Stop | foreach {Get-MsolRoleMember -RoleObjectId $_.ObjectID} | Where-Object {$null -ne $_.EmailAddress} | Select EmailAddress -Unique | Sort-Object EmailAddress
}
}
PROCESS {
if ($PSBoundParameters.ContainsKey("UserPrincipalName")) {
foreach ($MsolUser in $UserPrincipalName) {
try {
$User = Get-MsolUser -UserPrincipalName $MsolUser -ErrorAction Stop
if ($SkipAdminCheck) {
$isAdmin = "-"
} else {
if ($AdminUsers -match $User.UserPrincipalName) {
$isAdmin = $true
} else {
$isAdmin = $false
}
}
if ($User.StrongAuthenticationMethods) {
$MFAEnabled = $true
} else {
$MFAEnabled = $false
}
[PSCustomObject]@{
DisplayName = $User.DisplayName
UserPrincipalName = $User.UserPrincipalName
isAdmin = $isAdmin
MFAEnabled = $MFAEnabled
}
} catch {
[PSCustomObject]@{
DisplayName = '_NotSynced'
UserPrincipalName = $User
isAdmin = '-'
MFAEnabled = '-'
}
} finally {
$null = $User
$null = $isAdmin
$null = $MFAEnabled
}
}
} else {
$AllUsers = Get-MsolUser -MaxResults $MaxResults | Where-Object {$_.IsLicensed -eq $isLicensed}
foreach ($User in $AllUsers) {
if ($SkipAdminCheck) {
$isAdmin = "-"
} else {
if ($AdminUsers -match $User.UserPrincipalName) {
$isAdmin = $true
} else {
$isAdmin = $false
}
}
if ($User.StrongAuthenticationMethods) {
$MFAEnabled = $true
} else {
$MFAEnabled = $false
}
[PSCustomObject]@{
DisplayName = $User.DisplayName
UserPrincipalName = $User.UserPrincipalName
isAdmin = $isAdmin
MFAEnabled = $MFAEnabled
}
$null = $User
$null = $isAdmin
$null = $MFAEnabled
}
}
}
END {}
}
So that’s it. That’s how you get MFA status for Office365 / Azure for your domain. Hopefully you found this useful and if you did, don’t forget to check out our Youtube channel at @theSysadminChannel


Is there an updated how to for this script? I’m looking for the status of several users in a csv file. We have a large tenant +500K and I want to narrow my search to just the users in my file… ~100 users listed. Please bare in mind, I’m just now learning scripting… today…. 🙂 So if there is a better way to get a list of users from a large tenant and compare against the user’s in my CSV file… I’m all for it. And thank you!