Microsoft recently announced that on October 1, 2022 they are going to disable legacy authentication (basic auth) for all M365 tenants. With everything now moving to Modern Authentication and Microsoft Authentication Library (MSAL), previously Active Directory Authentication Library (ADAL) we should know how to disable those old authentication methods. Today, we’re actually going to cover the step by step methods to block legacy authentication Office 365.
Table Of Contents
- What is Legacy Authentication And Why We Should Block It
- How To See If Legacy Authentication Is Blocked in your Tenant
- Use Conditional Access To Block Legacy Authentication In Office 365
- Block Legacy Authentication Exchange Online
- Create an Authentication Policy to Disable Basic Authentication
- Disable IMAP/POP/Mapi/SMTPAuth protocols per mailbox
- Conclusion
What is Legacy Authentication And Why We Should Block It
I suppose before we go into detail on how to block it, we should probably address what it is. Legacy authentication is more or less self explanatory. By that I mean, it includes authentication methods that are superseded by todays modern authentication. In short, legacy authentication are authentication methods typically used by mail protocols such as IMAP, SMTP and POP3. Microsoft Office 2010 is an example client that uses legacy authentication.
The biggest take away here is that legacy authentication was highly active during a time where multi-factor authentication wasn’t really a thing. We’ve come a long way as far as security and auth methods go, but should still close those gaps because it can lead to open vulnerabilities in your environment.
To summarize, legacy authentication does not enforce multi-factor authentication (MFA) so it gives attackers a preferred attack vector to exploit. This is the biggest reason why we want to block legacy authentication. With that said, we can now get into the modern (and preferred) methods to blocking legacy authentication using conditional access policies.
How To See If Legacy Authentication Is Blocked in your Tenant
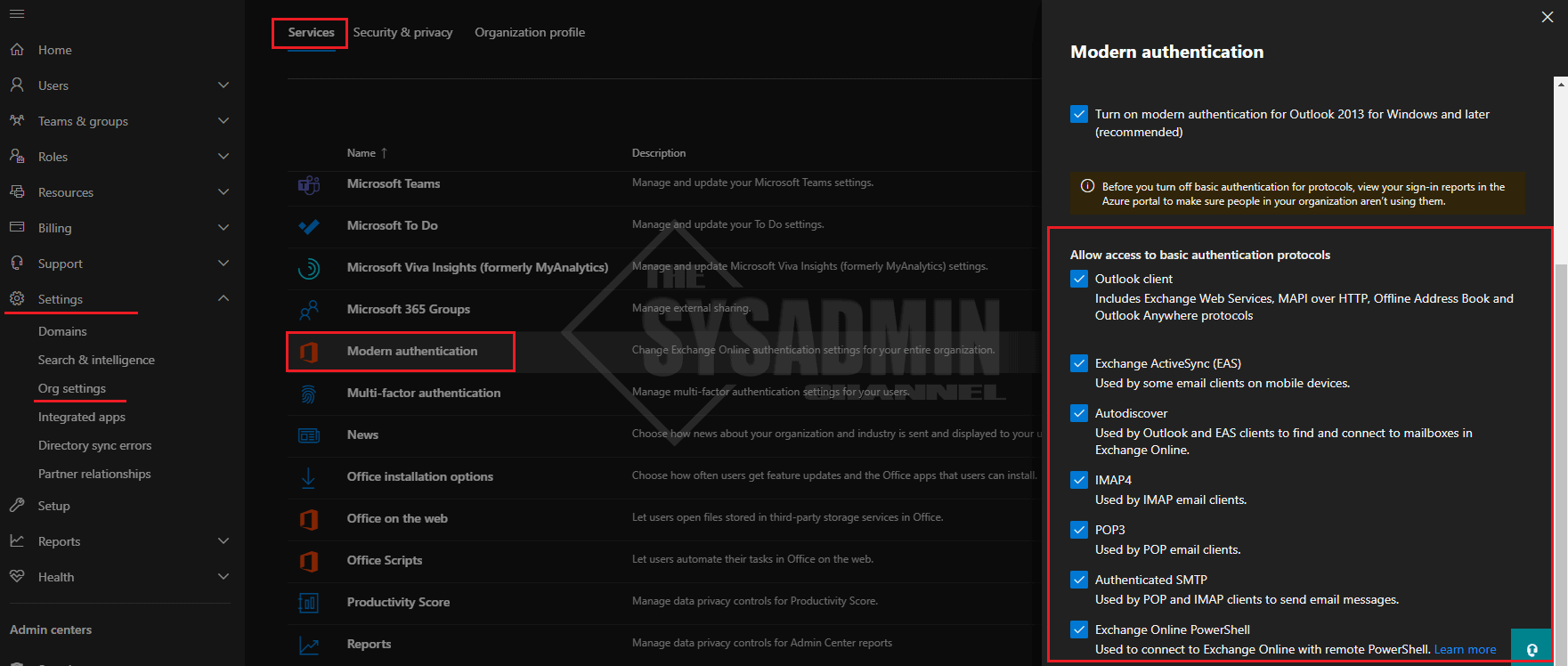
Now before you go through your testing it might be a good idea to check whether basic authentication is blocked in your tenant to begin with. Microsoft has already stated that if they don’t see any authentication requests using these older protocols, they’re going to disable it by default. In my tenant I wasn’t using so it was actually already turned off. To save you the headache, here are the steps to check if basic authentication is enabled in your tenant.
- Navigate to https://admin.microsoft.com/ to get to the Office 365 admin portal
- Next navigate to settings -> Org Settings -> Services -> Modern Authentication
Use Conditional Access To Block Legacy Authentication In Office 365
Now that we understand the why, let’s get into the how portion of this article. We’re going to assume you have permissions to create conditional access policies.
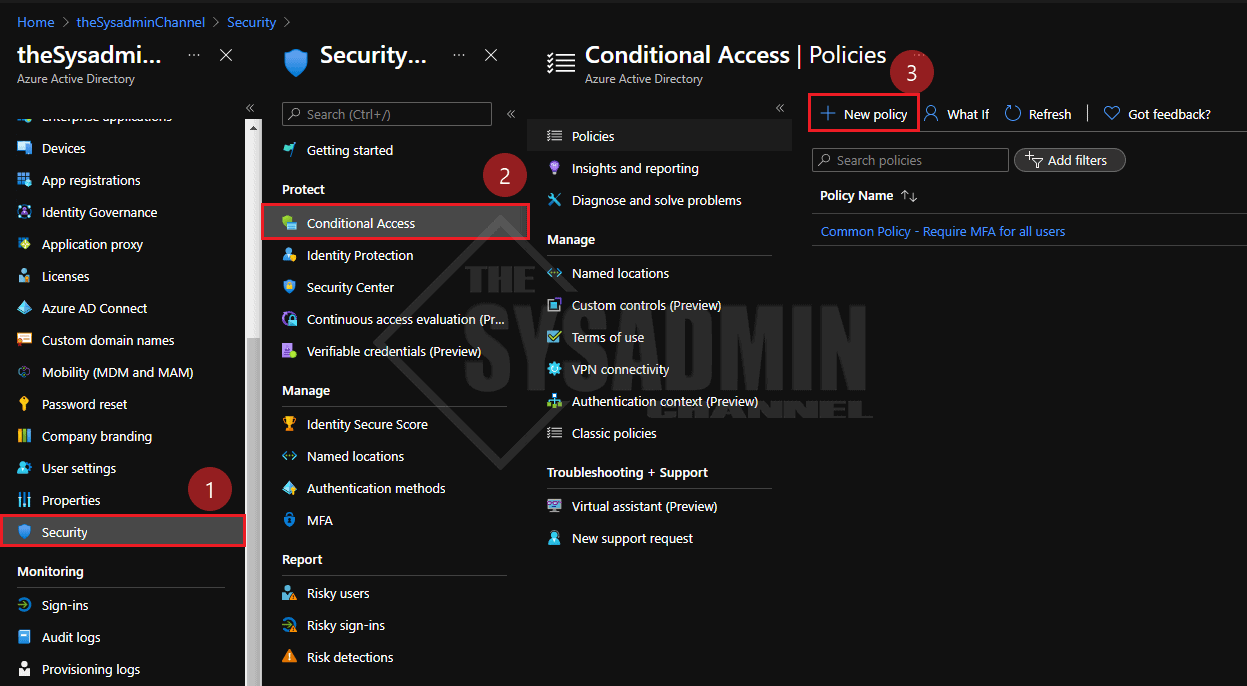
- In Azure, navigate to Azure Active Directory -> Security -> Conditional Access -> Create a New Policy
- Direct Link: https://portal.azure.com/#blade/Microsoft_AAD_IAM/ConditionalAccessBlade/Policies
- We’ll name this policy, Common Policy – Block Legacy Authentication
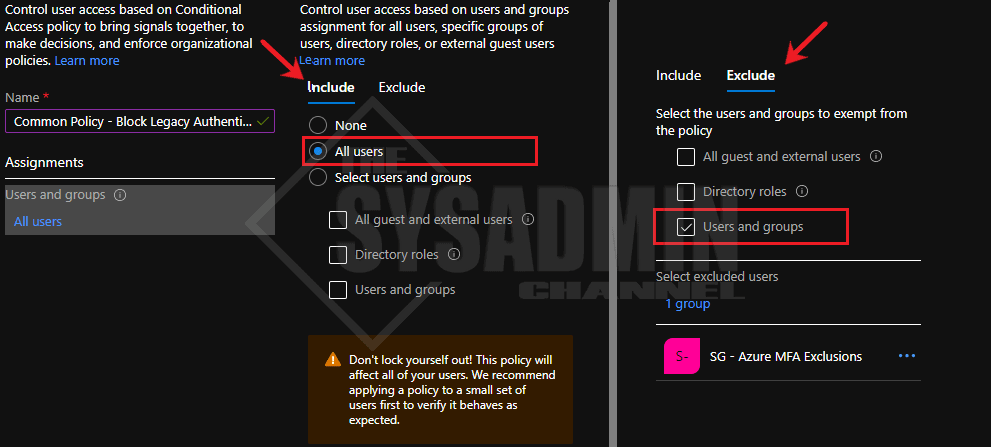
- Under Users and groups:
- Under Include: We’ll select all users
- Under Exclude: We’ll want to exclude our exclusions group – e.g. break glass/service accounts
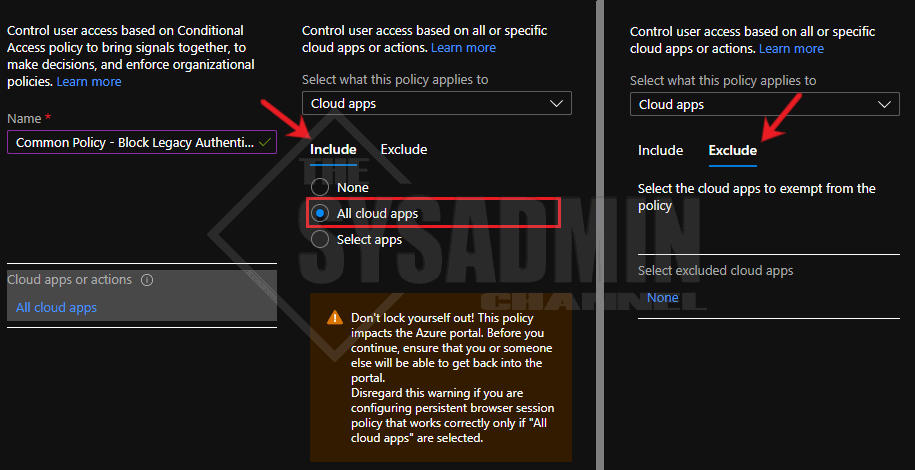
- Cloud apps or actions:
- Under Include: We’ll select all cloud apps
- Under Exclude: We’ll want to leave this blank
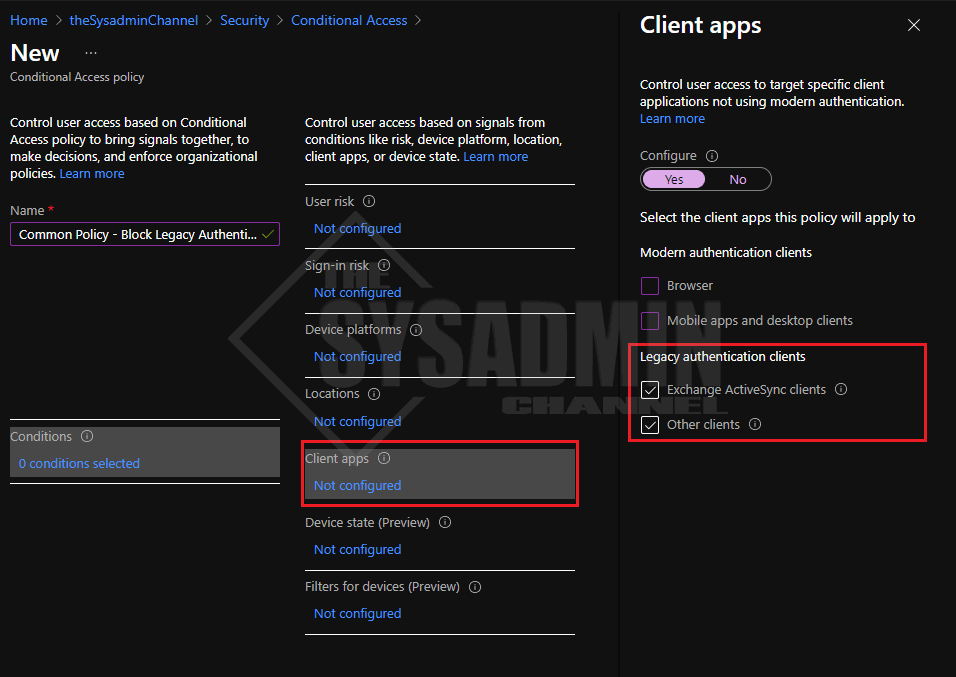
- Conditions -> Client apps:
- Select “Yes” to configure policy
- Unselect Browser and Mobile apps and desktop clients
- Leave Exchange ActiveSync clients checked
- Leave Other clients checked
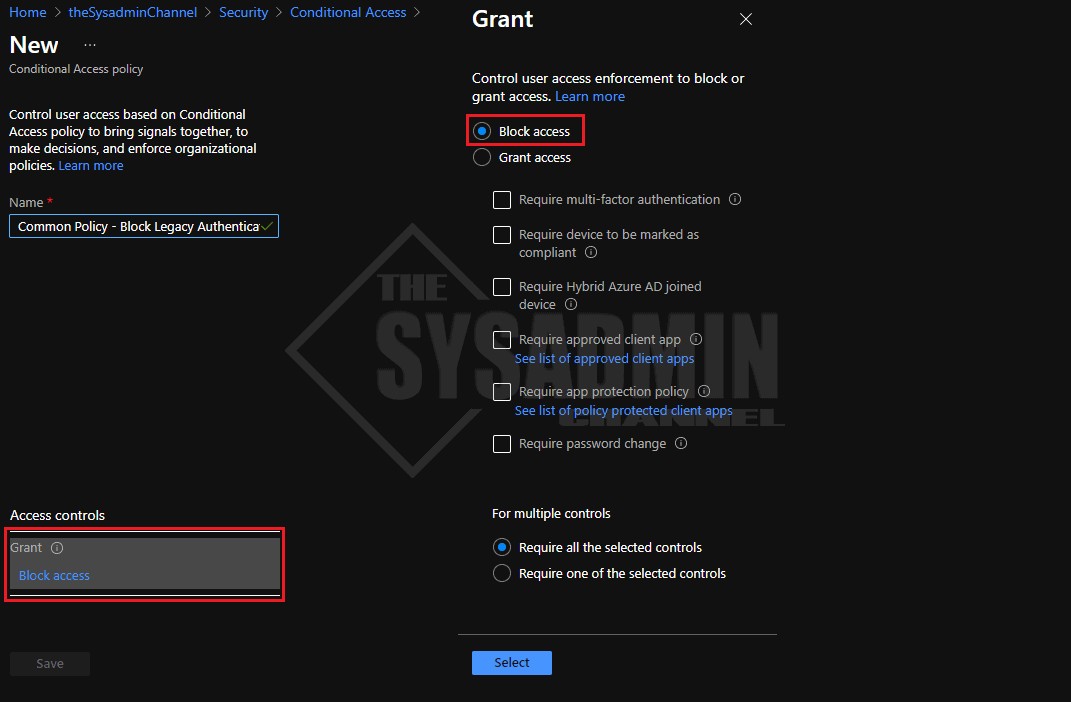
- Grant:
- Select Block Access
For the final step, set the policy to Report-only so you can have some insights before enabling the policy. This will give you a heads up as to who is still using legacy authentication and at least give them some kind of notice to stop. Otherwise, if you’re brave, turn it off and apply the scream test which is also just as effective as finding out who is still using it.
Block Legacy Authentication Exchange Online
In addition to conditional access, we should also consider disabling the legacy auth methods in Exchange Online itself. There are several ways we can about it and we’ll cover those methods as well. However, here is a quick overview.
- Using an Authentication Policy
- Apply it as the default organization policy
- Apply it as a per user policy
- Disable IMAP/POP/Mapi/SMTPAuth protocols per mailbox
Create an Authentication Policy to Disable Basic Authentication
Being able to create an authentication policy would be able to help you not only identify who is using the policy, but set a standard for your setup. The command to create an auth policy is New-AuthenticationPolicy. Let’s cover two scenarios for enabling and disabling the required protocols.
#Create a Block Legacy Authentication Policy New-AuthenticationPolicy -Name "Block Legacy Authentication" #Create an Allow All Legacy Authentication Policy New-AuthenticationPolicy -Name "Allow All Legacy Authentication" -AllowBasicAuthRpc -AllowBasicAuthPop -AllowBasicAuthSmtp -AllowBasicAuthMapi -AllowBasicAuthImap -AllowBasicAuthAutodiscover -AllowBasicAuthPowershell -AllowBasicAuthActiveSync -AllowBasicAuthOfflineAddressBook -AllowBasicAuthReportingWebServices -AllowBasicAuthOutlookService -AllowBasicAuthWebServices #Set the authentication policy as the default authentication policy for your organization Set-OrganizationConfig -DefaultAuthenticationPolicy 'Block Legacy Authentication' #Set the authentication policy on a per user basis Set-User jsnow -AuthenticationPolicy 'Block Legacy Authentication' #Have the policy take effect within the next 30 minutes. By default it can take up to 24 hours. Set-User -Identity jsnow -STSRefreshTokensValidFrom (Get-Date).ToUniversalTime()
Disable IMAP/POP/Mapi/SMTPAuth protocols per mailbox
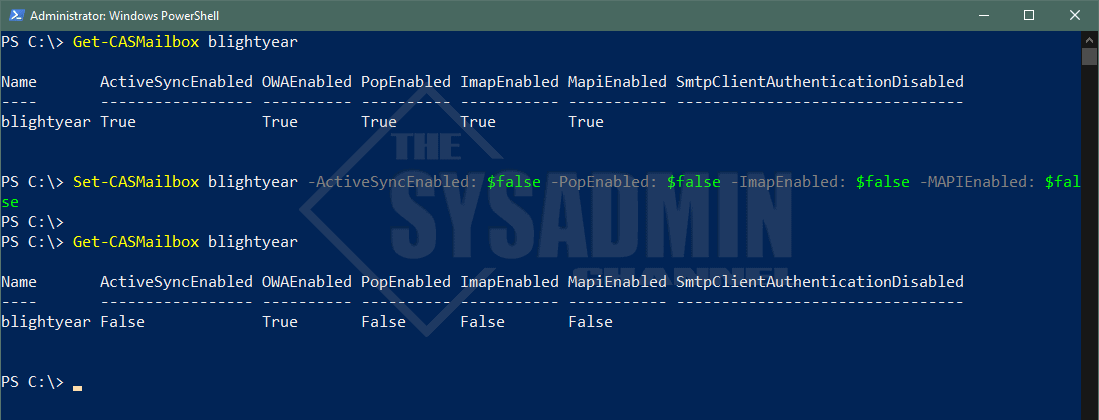
Another alternative to the authentication method is to disable the protocols for each individual mailbox. This can be done using the Set-CASMailbox command for each of the mailboxes you’d want to disable.
PS C:\> Get-CASMailbox blightyear Name ActiveSyncEnabled OWAEnabled PopEnabled ImapEnabled MapiEnabled SmtpClientAuthenticationDisabled ---- ----------------- ---------- ---------- ----------- ----------- -------------------------------- blightyear True True True True True PS C:\> Set-CASMailbox blightyear -ActiveSyncEnabled: $false -PopEnabled: $false -ImapEnabled: $false -MAPIEnabled: $false PS C:\> PS C:\> Get-CASMailbox blightyear Name ActiveSyncEnabled OWAEnabled PopEnabled ImapEnabled MapiEnabled SmtpClientAuthenticationDisabled ---- ----------------- ---------- ---------- ----------- ----------- -------------------------------- blightyear False True False False False
Conclusion
That’s it. Now we know how to block legacy authentication using conditional access policies in Azure Active Directory. For more posts on conditional access or Azure AD in general, be sure to check out our gallery of Azure Active Directory.


Hi, Would you know how to get exchange active sync working using Nokia Email client (Symbian Belle)? Recently it just stopped syncing.