In this day and age, it is imperative that organizations enforce MFA to enhance their security posture. As threat actors become equipped with more sophisticated tools, we need to ensure we enforce strong authentication requirements for all users, all the time. However, more MFA prompts does not equate to better security. In fact it is quite the opposite, but we’ll touch on that later. Today we’re going to cover how to securely reduce MFA Prompts in Azure AD.
Table Of Contents
Requirements
If you’ve implemented MFA across the entire org or you’re just about to go down that path it is important to know there are tools and licenses you should have in place to make the experience a much better one. Let’s touch on those a bit now.
While Azure AD P2 licenses are preferred, having a P1 license will grant you access to conditional policies, Log Analytics and other Azure AD features. Technically all you need is a single P2 license to enable these features however, all users that are using the features should be licensed for it.
What NOT to do if Azure MFA Keeps Prompting
Before we go into detail on what MFA prompt frequency best practices are and what we can do suppress them, let’s take some time to discuss what we should NOT be doing. These “don’ts” are called out because of the security implications it can have on your AAD environment.
I see it time and time again when scrolling through Twitter, Reddit or other articles, people recommend whitelisting their office public IP addresses as a way to bypass MFA. After all, if you’re in a building that probably requires a badge to gain access, we should be good right? WRONG!
Tailgating does happen in the wild and if you set policies to bypass MFA for people in the office, you have effectively punched security holes into your environment. Aside from that, many office buildings have guest wi-fi networks for their visitors that someone can easily connect to. If the guest network is configured to use the same outbound public IP as the corporate network, you’ve just opened yourself up to a potential world of hurt. If that still doesn’t convince you, figuring out how to spoof a public IP address is just a Google search away so these methods should be avoided at all costs.
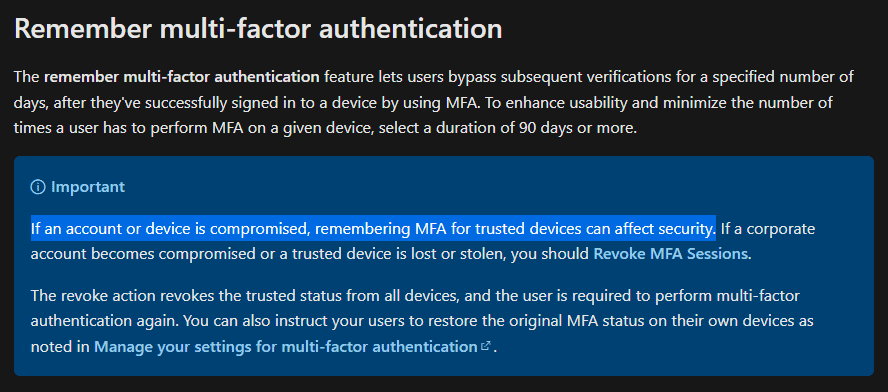
Another setting we want to avoid is to keep the “remember multi-factor authentication on trusted device” setting enabled in the legacy Azure service settings portal. While it does what it says and reduces the number of MFA prompts you will get, it is not the best approach for what we are trying to accomplish. Microsoft also calls this out on their documentation.
I should also mention that requiring an MFA prompt for every sign in, or otherwise purposely overly prompting for MFA can be just as bad. When someone is constantly getting prompted for MFA, they tend to become numb to the process and mindlessly hit approve. There are ways to mitigate MFA fatigue attacks by implementing MFA number matching but the point still stands. More MFA prompts does not equate to more security.
To summarize, here is what we should NOT be doing to reduce MFA prompts in Azure AD:
- Do NOT whitelist public IPs to bypass MFA
- Do NOT enable remember multi-factor authentication on trusted device
- Do NOT purposely over prompt for MFA
Authentication Prompts Analysis: See Whos Is Getting Prompted for MFA
Azure AD is a platform that can be used as a 100% cloud only solution for your users, or a hybrid solution if you’re still maintaining an On-Premises environment. With that said, it also comes equipped with its own audit logging and monitoring tools (when you have Azure AD P1/P2 licenses) so we can use Azure AD workbooks to get insights on who is actually getting prompted for MFA and what applications are prompting them.
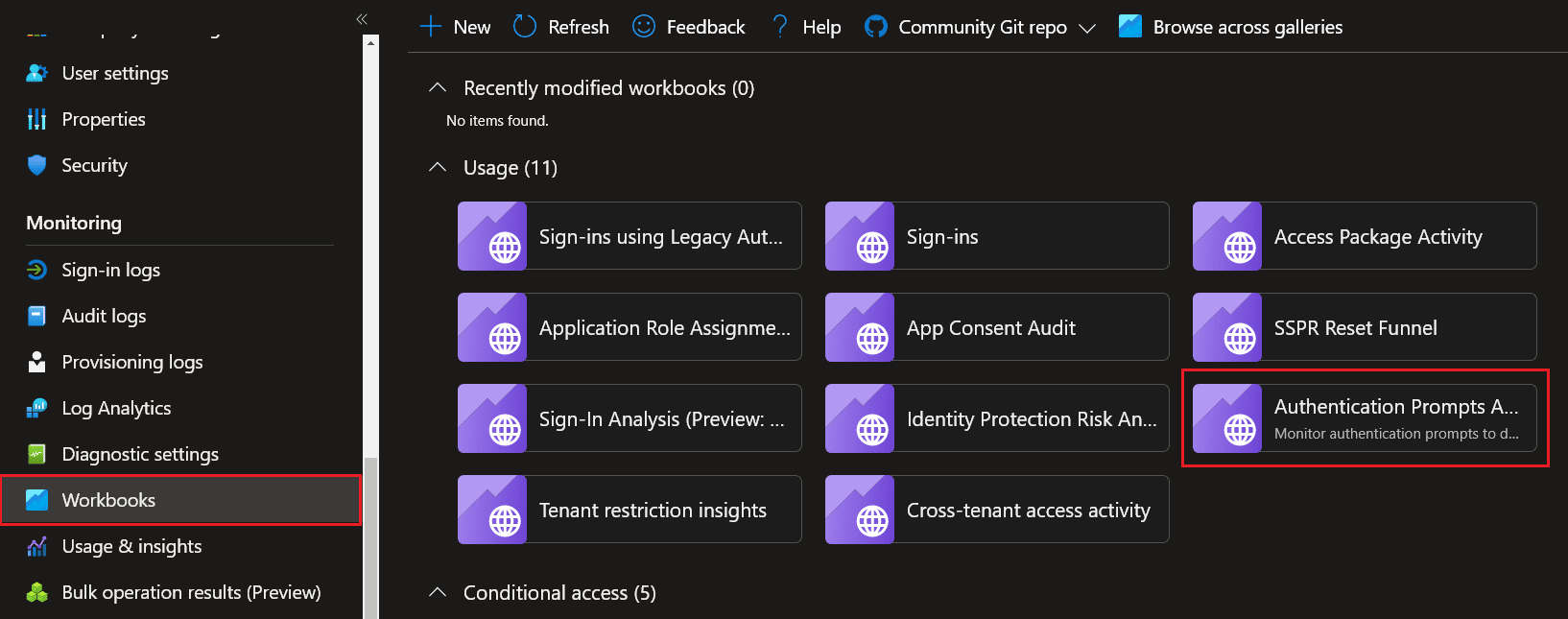
Azure AD has done all of the hard work for you and conveniently created an authentication prompts analysis workbook.
To access it:
- Navigate to Azure AD → Workbooks
- Select Authentication Prompts Analysis workbook
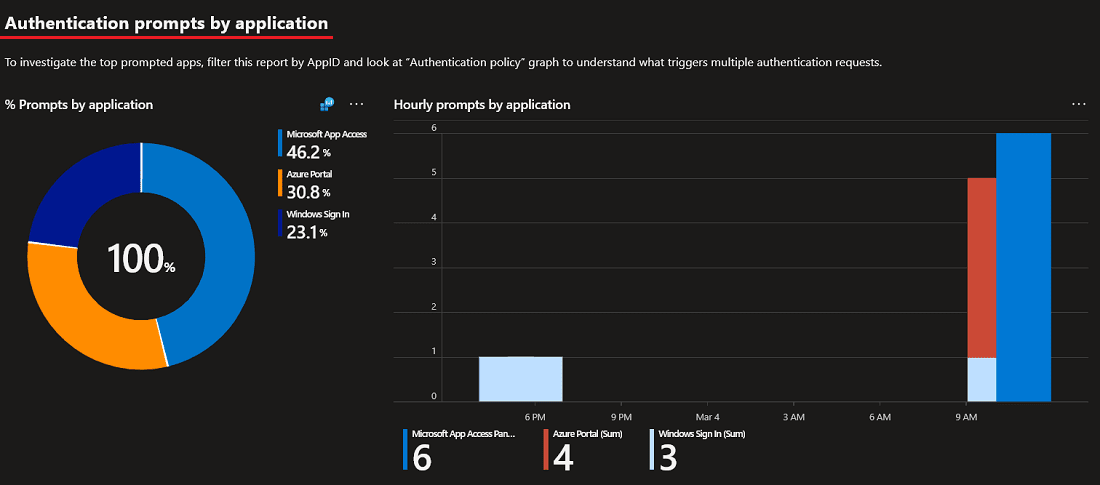
If you have time I would highly suggest you take a look at the data. My only suggestion for the workbook would be that they remove “Windows Sign In” attempts since that can kind of skew the data. Windows Sign In is when a user signs in their Windows device so this will not require MFA. However, the workbook lays out several categories for prompts.
Those include:
- Authentication prompts by authentication method
- Authentication prompts by device
- Authentication prompts by user
- Authentication prompts by application
- Authentication prompts by process detail
How to Reduce MFA Prompts in Azure AD
Now that we’ve covered who is getting prompted for MFA and more importantly, what NOT to do, let’s focus on what we should be doing and the best practices for how to reduce MFA prompts in Azure AD. Remember, Azure AD is the Identity Provider (IdP) so this applies to all Azure AD cloud applications. If Office 365 MFA prompts every time, this will ensure the prompts are significantly lowered when implemented successfully.
Windows Hello for Business
If you’re looking for best practices to reduce MFA Prompts in Azure AD, Windows Hello for Business is by far the BEST way to securely accomplish this. With Windows Hello for Business enabled, you’re always using strong authentication and the MFA claims are satisfied automatically.
This is because when you sign in with WH4B, a Primary Refresh Token (PRT) gets generated at that initial sign in and is presented to all other Azure AD applications when they’re accessed. This allows for a truly seamless SSO experience and even better, it provides a fantastic user experience. If you’ve never heard of a PRT, I would highly suggest you take the time to learn more about Primary Refresh Tokens. The documentation for this is phenomenal.
Windows 10 Accounts Chrome extension
While Edge handles this capability natively in the browser, It strongly recommended that those hard chargers using Google Chrome have the Windows 10 Accounts Chrome extensions deployed on their machine. If you are NOT using Windows Hello for Business, you will need to MFA to that initial application which will create a PRT that can be used on any subsequent applications.
If you ARE using WH4B, you will still need to deploy this plugin because Chrome doesn’t natively support a Primary Refresh Token. As an optional step, you can enable this in incognito mode so users can continue to use their PRT while in private-mode. Again, Microsoft Edge handles this natively but this is good to know.
Finally, and probably more importantly, in order to successfully create PRT, the devices will need to be at a minimum Azure AD registered. Non registered devices will not be given a PRT so those devices will continue to be prompted.
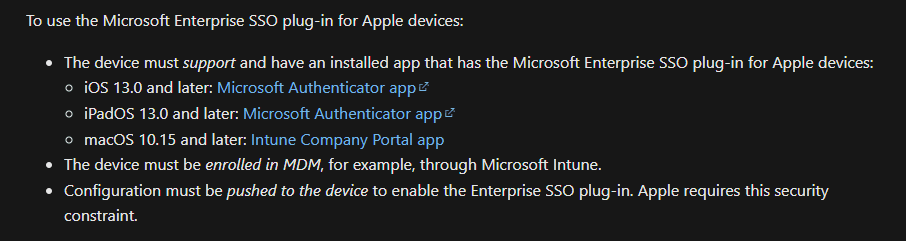
Enterprise SSO for Apple Devices
We’ve covered what to do for Windows devices, but what is the recommendation for MacOS and iOS devices? After all, it is quite common to see an organization operate with a mix of Apple, Windows and Linux devices in their environment. The answer is Enterprise SSO for Apple devices. There a few requirements that are listed in the documentation so we’ll summarize that here.
An important item to note is if your primary MDM solution is not Microsoft Intune, you will need to deploy the SSO extension AND ensure your device is enrolled in Intune. It doesn’t have to be managed by Intune, but it must be enrolled so Azure can see the device.
Conclusion
Hopefully this article was able to provide useful insight on how to reduce the number of MFA prompts using secure best practices. Remember, the goal is to require strong authentication all the time, on every application. However, the trick is to use these methods listed above so MFA requirements are satisfied and you’re no longer being prompted.
I personally use Windows Hello for Business and I am prompted once every several months on my standard account because my MFA requirement is already satisfied by claim in the token.