Microsoft recently released a feature to create custom extensions in Entra Identity Governance that can allow users to kick off custom processes using Logic Apps. If you’re not familiar with what a Logic App is, it is a low code/no code integration automation platform that allows you to run processes on a server-less framework.
This is great because Logic Apps can provide an endless possibility of automation workflows using built-in connectors. If you prefer to run code to handle the automation, there’s a connector for Azure Automation and even Function Apps.
Table Of Contents
Requirements
Whether you’re creating the very first custom extension or adding additional extensions to your catalog, there are a few things in place you will need so everything runs smoothly. Let’s touch on those items now.
First things first, you’ll need to have an Azure Resource Group created so you can host your newly created Logic Apps. It would be preferred to be an owner of that RG so you can grant permissions to the Managed Identities you will eventually create with your LA.
If you prefer to use Logic Apps as the conduit to other automation platforms like Azure Automation or Function Apps, the Logic App Managed Identity will need the appropriate permissions to that resource. For these use cases, I personally like to have my Logic Apps, Function Apps and automation runbooks under the same resource group.
Create The First Custom Extension
If this is the first time you’ve ever created a custom extension for an Entitlement Management access package then you’re definitely in luck. We’ll walk through the steps on exactly how to do that.
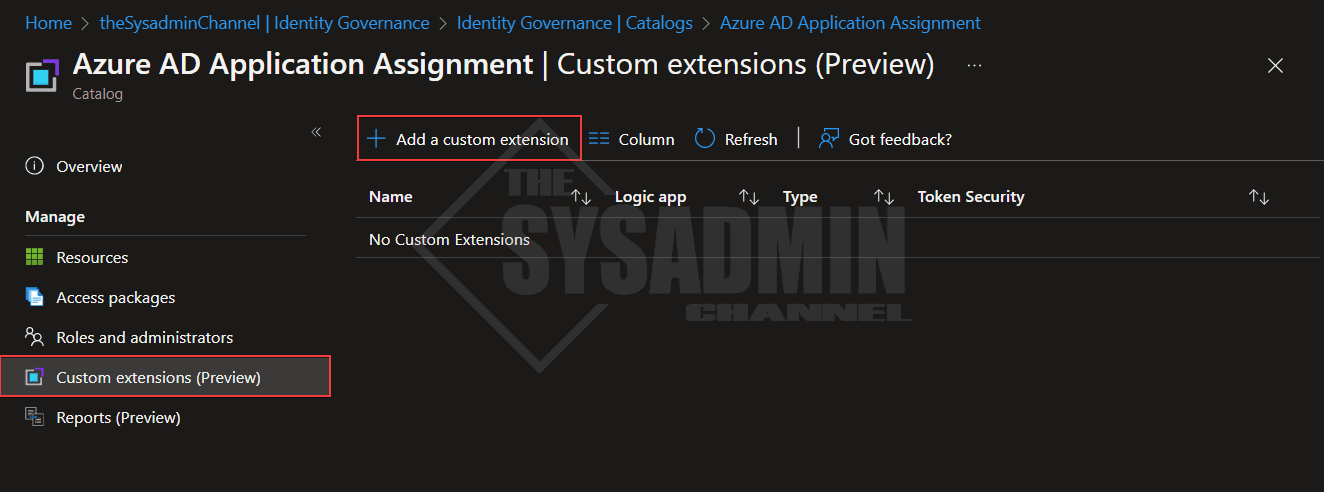
Within the Catalog:
- Click on Custom extensions
- Add a new custom extension
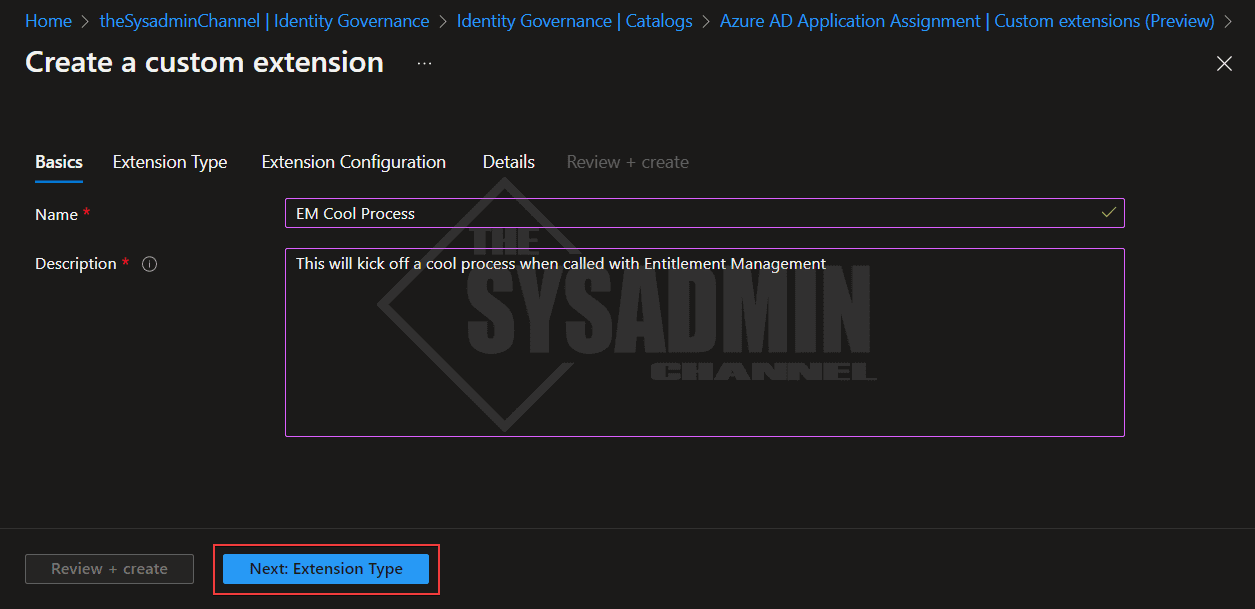
- Enter a name and description that best describes what the custom extension will be doing
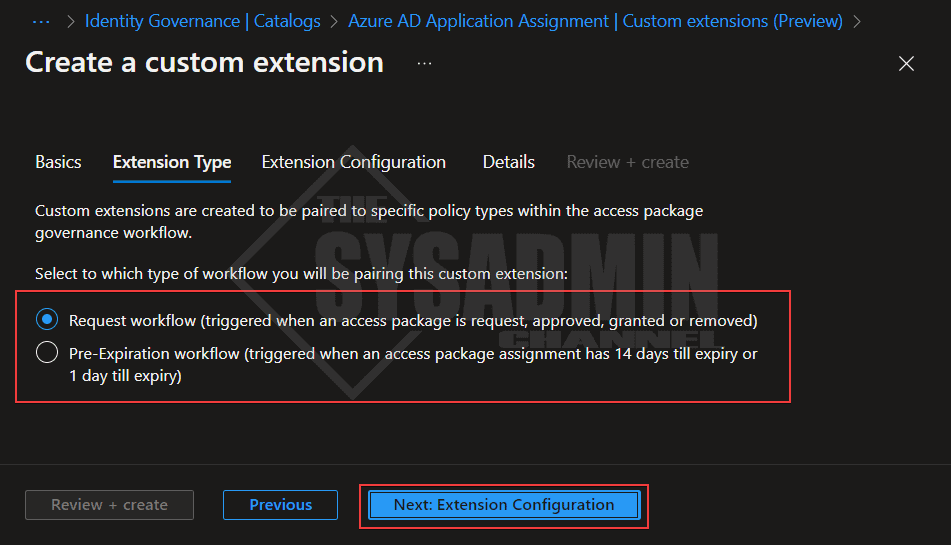
- Select the option if you want to run the request workflow or pre-expiration
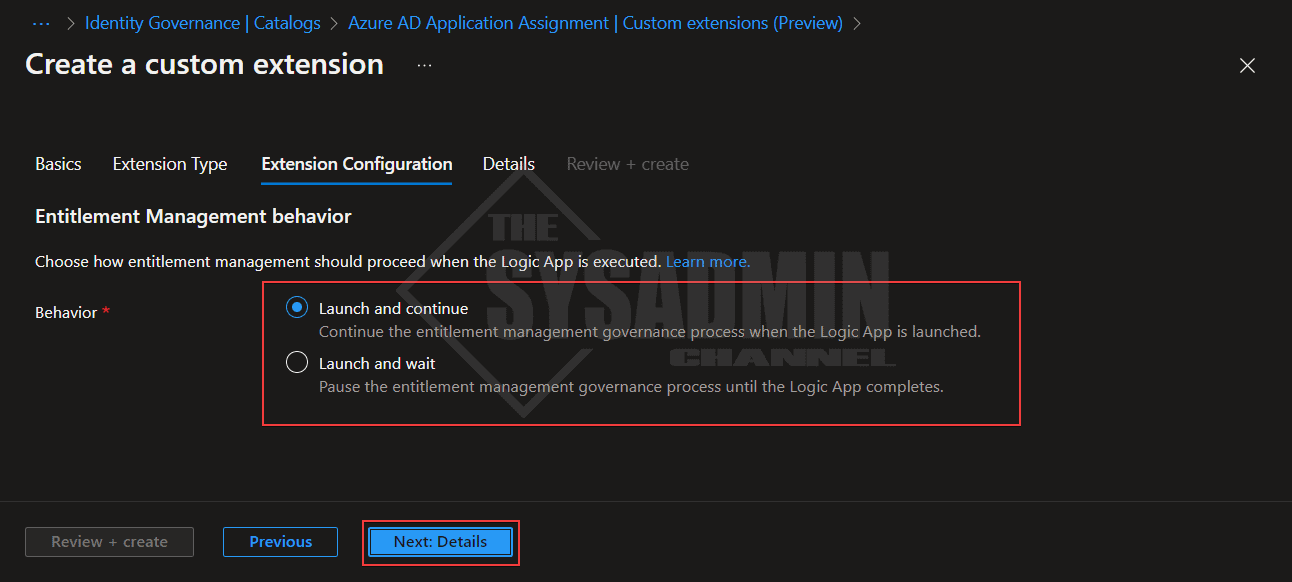
- Select the option if you want to launch and continue or launch and wait
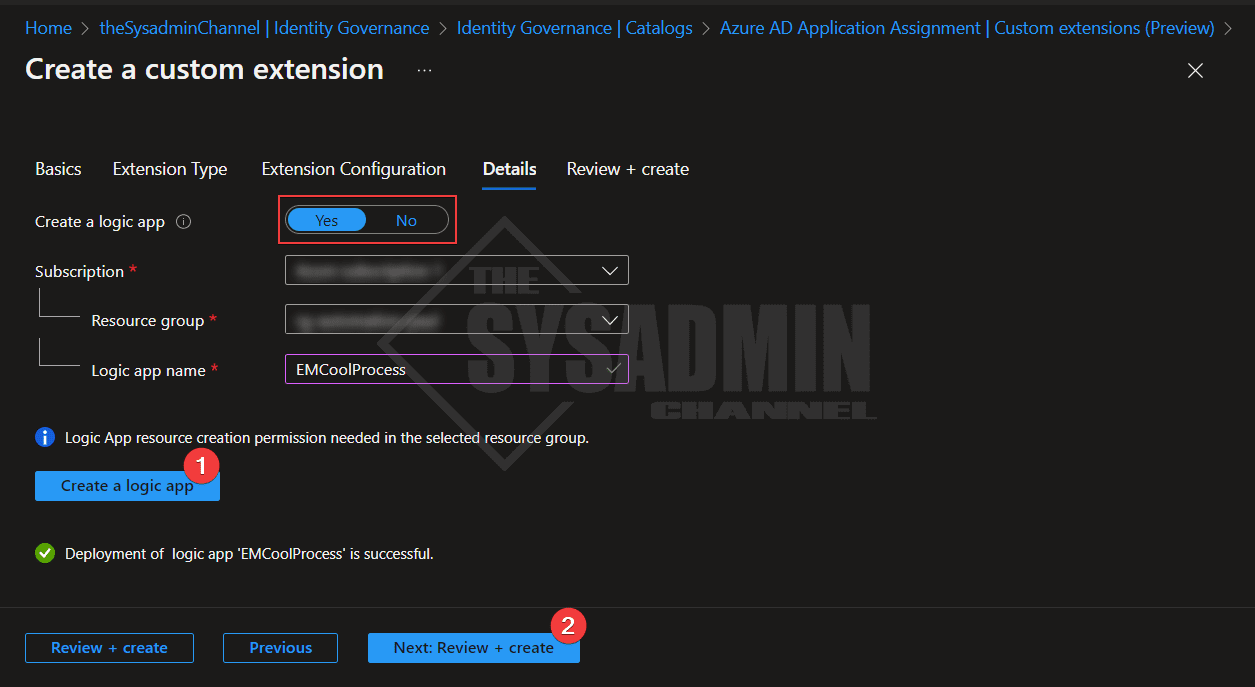
- Select Yes to create a logic app
- Select the Azure subscription and resource group
- Enter a name that describes the process (I like to have the same name as the extension)
- Click create a logic app
- Click next to review and create
Importing a Custom Extension on a Different Catalog
Organizing your catalogs by processes or by teams is important for keeping everything in order, but what if you wanted to use the same workflow on a different catalog? By default there is not an “import” button that can magically create the same custom extension on a different catalog, however it is possible by simply creating a new extension on the catalog you want to run that Logic App in.
The steps to accomplish that are pretty much the same as above. You’ll need to create a custom extension, populate the fields just as you did before. The difference is in the details. Let’s take that a step further.
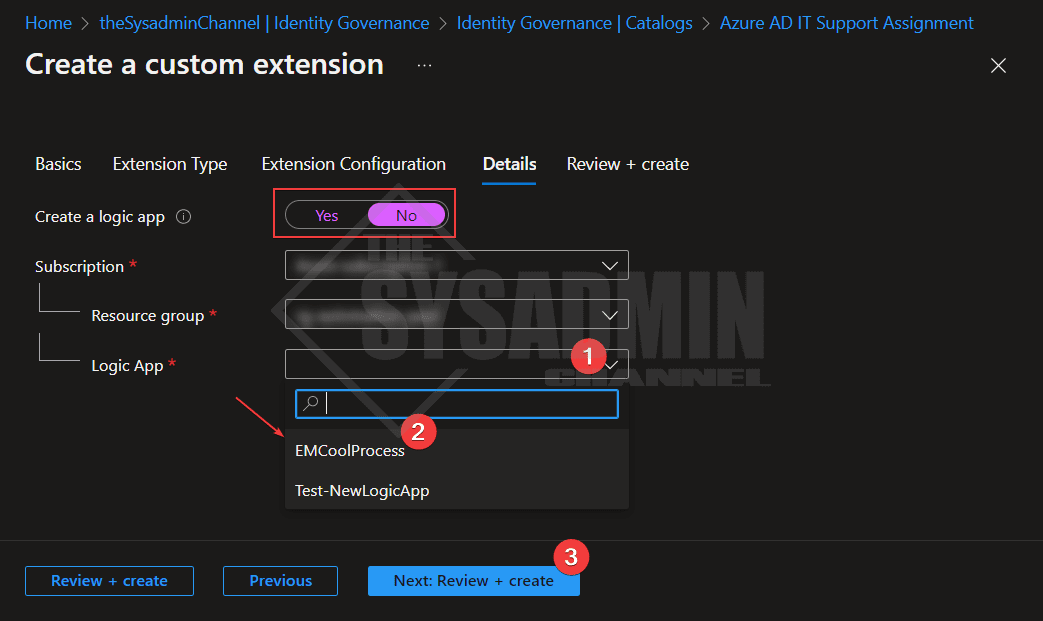
In the new catalog, under the details tab:
- Select no to create a logic app
- Select the same subscription and resource group that the Logic App is hosted in
- Under the Logic App drop down menu, select the previously created LA
- Select next to review and create
View The Logic App And Create A Workflow
Now that we know how to create and import an existing custom extension created by Entitlement Management, let’s look into accessing it so we can outline what exactly we want it to do.
On the custom extensions page, click on the link to the Logic App.
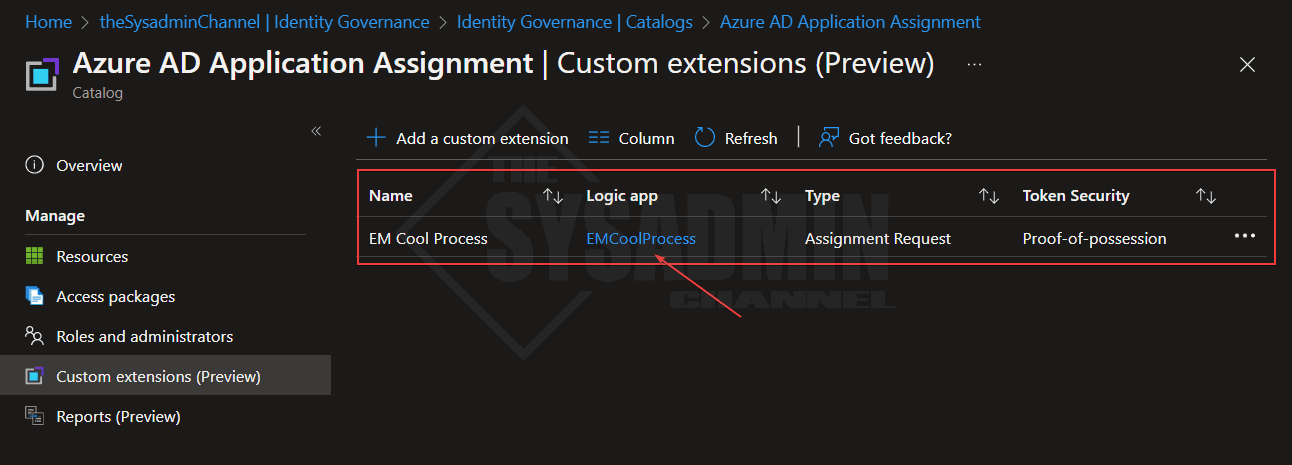
This should take you to the Logic App itself where you can modify everything as needed. We won’t cover the details of the logic app workflow here since that’s a whole another platform to discuss, however, I will note that there have been significant improvements for the overall process.
Not only is it much more secure (we’ll touch on that in a bit), but there are also many more properties available in the payload going to the logic app. An example of this is if you’re asking questions in the package, the answers are now available by default.
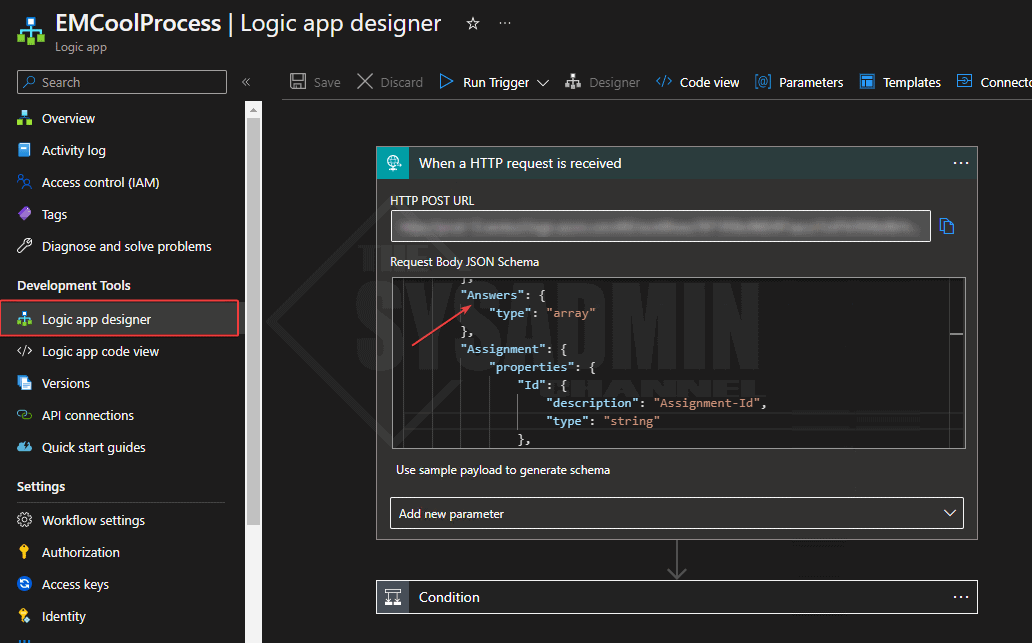
Regarding the security improvements, this is fantastic because it now uses an Azure AD Proof-of-Possession token that mitigates against token theft. Here is a snippet from the GitHub Page
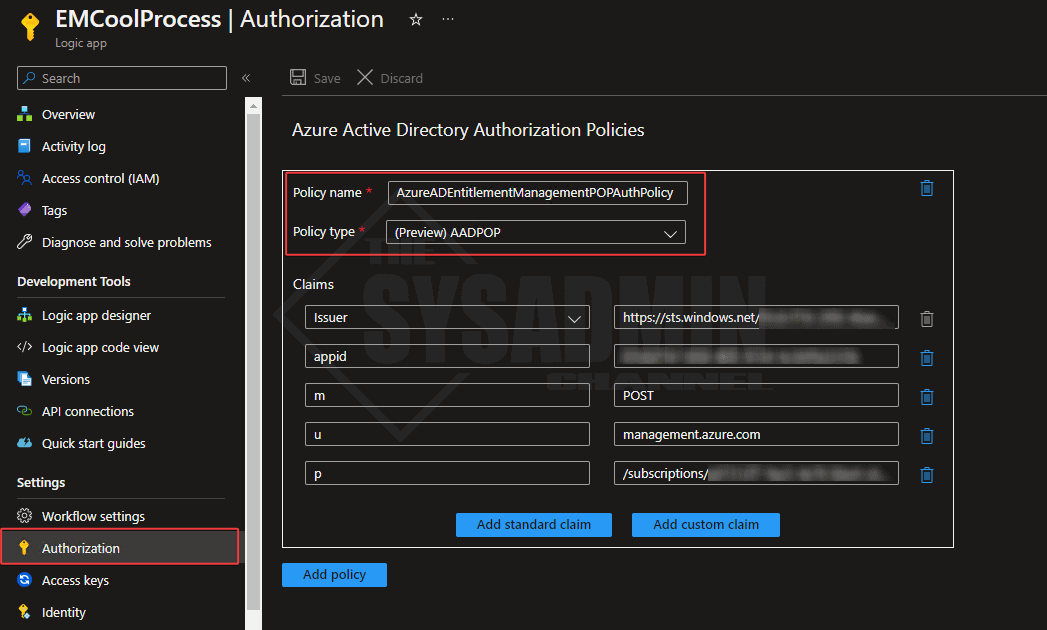
If you click on the Authorization page on the left pane, you can see how it’s setup. Here’s an outline of what mine looks like. Note: This is added by default so no need to modify anything 🙂
Apply the Logic App to an Access Package
Assuming you’ve already done the work to update the logic app to your liking, we’re now in a place where we can apply the the custom extension to an access package so let’s touch on how to do that.
First, You’ll need to create an access package along with the assignment policy under the catalog where you’ve created/imported your logic app. At the end of the wizard you should see the option to add a custom extension.
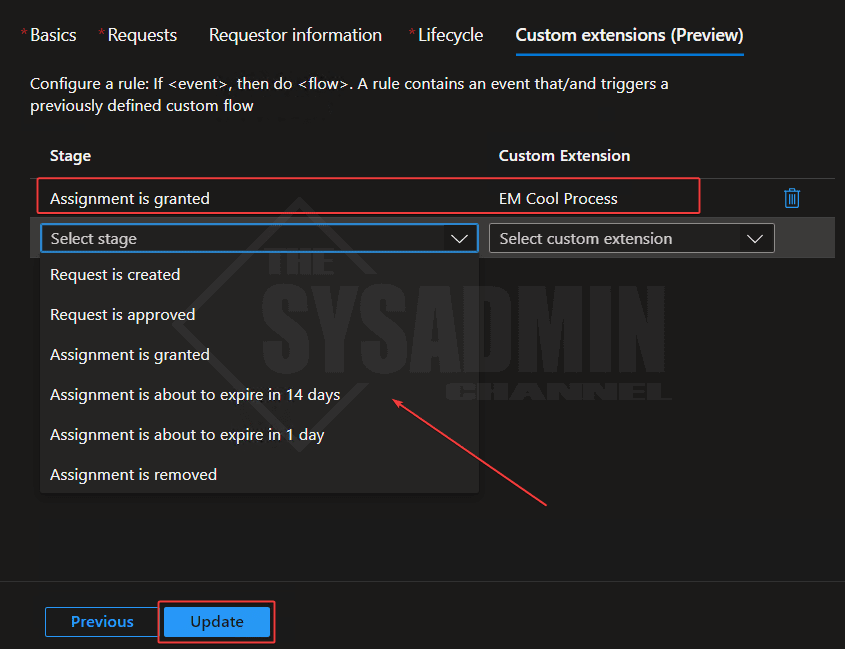
Those specific stages are:
- Request is created
- Request is approved
- Assignment is granted
- Assignment is about to expire in 14 days
- Assignment is about to expire in 1 day
- Assignment is removed
Each stage has its purpose so you definitely have the flexibility extend a process around a specific stage. In my sample above, I set the action to run EM Cool Process to run when assignment has been granted.
Conclusion
Hopefully you now have a great understanding on how to create custom extensions in Entra Identity Governance. As someone who uses this in the real world, this is one of the features I love the most about Azure AD because it’s so versatile and allows you to implement a self service framework without the hassle of maintaining a frontend or backend. It’s built into the tool.