Get Last Logon Date For All Users in Your Domain. It seems simple right? In many of the environments I’ve walked into there have been users that haven’t logged into the domain in a certain number of months. Some users more recent than others but I have seen some as bad as a couple of years, yet the accounts were still not disabled. For me personally, this is probably one of my biggest pet peeves.
I don’t know why, but I don’t like to see stale accounts just there in the mix with all the accounts that logon on a regular basis. I understand that some can be lab accounts, others can be test accounts that get used from time to time but for the most part, it’s Nancy from Accounting that quit 3 years ago and her account is still being used by Mary because there wasn’t a proper term procedure in place.
We’ll get to the automation of the term procedure in another post but this should be done. For one, it’s a huge SOX violation and two, it gives you a better overview of what’s in your environment. So for this, we will use the LastLogonDate and LastLogon attributes in Active Directory to get last logon date for users in your domain.
What is last logon in Active Directory
So what is last logon in Active Directory? In simple terms, it’s a time stamp representation of the last time a domain controller successfully authenticated the user or computer object.
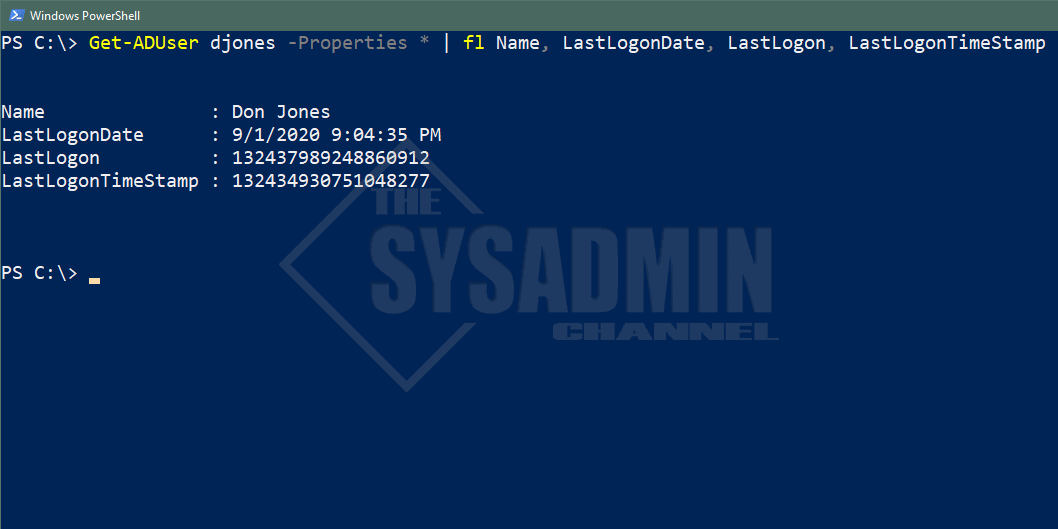
There are 3 basic attributes that tell you when the last time an object last authenticated against a Domain Controller. They are the LastLogonDate, LastLogon and the LastLogonTimeStamp.
LastLogon vs LastLogonTimeStamp vs LastLogonDate
If you’ve been doing your research I’m sure you’ve come across articles saying to use LastLogonTimeStamp because it replicates across all DCs and gives you a more accurate reading of when the last time the user logged on. However, this may not always be the case, simply because it only updates when “it feels like it” to put it into lamens terms. LastLogonTimeStamp will give you a rough ballpark of about 2 weeks to see when the user has logged on. When querying the LastLogonTimeStamp, it also uses an unconverted timestamp so we would have to do some Powershell magic to convert it to something our brains understand.
The LastLogonDate is a replica of the LastLogonTimeStamp, however, the output is a human readable date format that we can understand. I should also note that this attribute is not only used for the logins, but rather the last time it accessed something on the network. So for example, let’s say Johnny, the remote sales guy, is only able to use VPN to connect to the network.
When he initially fires up his laptop and logs in, he is logging in with his cached credentials so he will never need authenticate to a DC, thus a LastLogon attribute won’t necessarily get updated. It could have been years since he was at HQ and actually authenticated against a DC to login so sometimes this is not always accurate either.
This is why I prefer to use the LastLogonDate attribute because even though Johnny never authenticated against a DC, he was still using resources on the network so his LastLogonDate attribute will get updated. I should note that just like LastLogonTimeStamp, LastLogonDate doesn’t get updated every single the user logs in. It will give you a 2 week window of when they last accessed something on the network. Whether it be email, network drives, remote desktop etc..
Get Last Logon Date with Powershell
So there are a couple of ways we can tackle this problem. If we’re only querying a single user I would say it’s best to use the LastLogon attribute because we can query against multiple DCs to get the most updated login attribute. If we’re querying multiple users (everything in the domain for example) we should be using the LastLogonDate attribute because it will not bog down the DC with requests and the results can be output fairly quickly. So how can we achieve this?
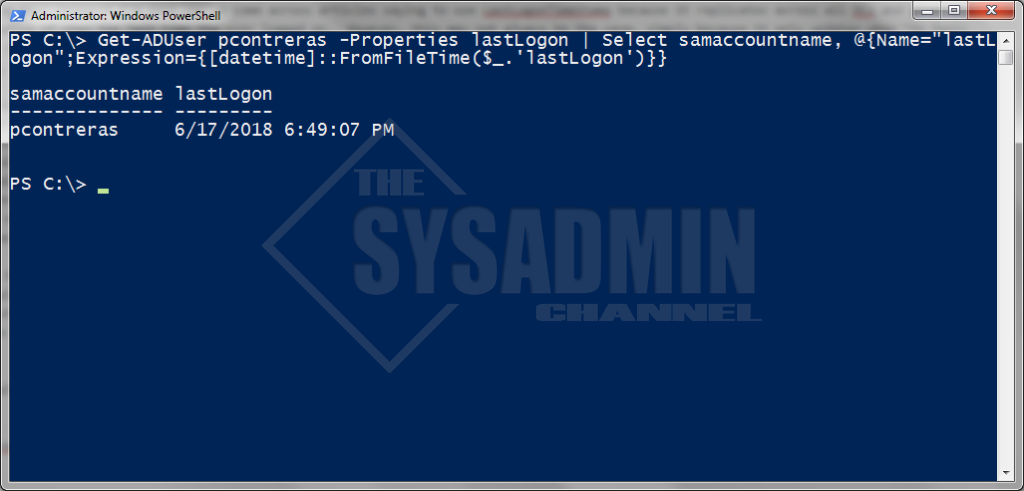
LastLogon Example with Powershell
Get-ADUser pcontreras -Properties lastLogon | Select samaccountname, @{Name="lastLogon";Expression={[datetime]::FromFileTime($_.'lastLogon')}}
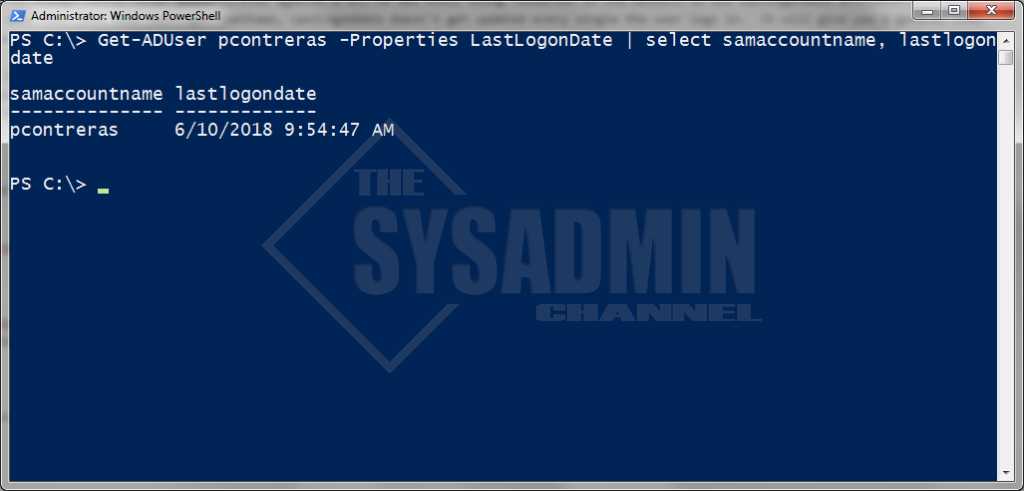
LastLogonDate Example with Powershell
Get-ADUser pcontreras -Properties LastLogonDate | select samaccountname, lastlogondate
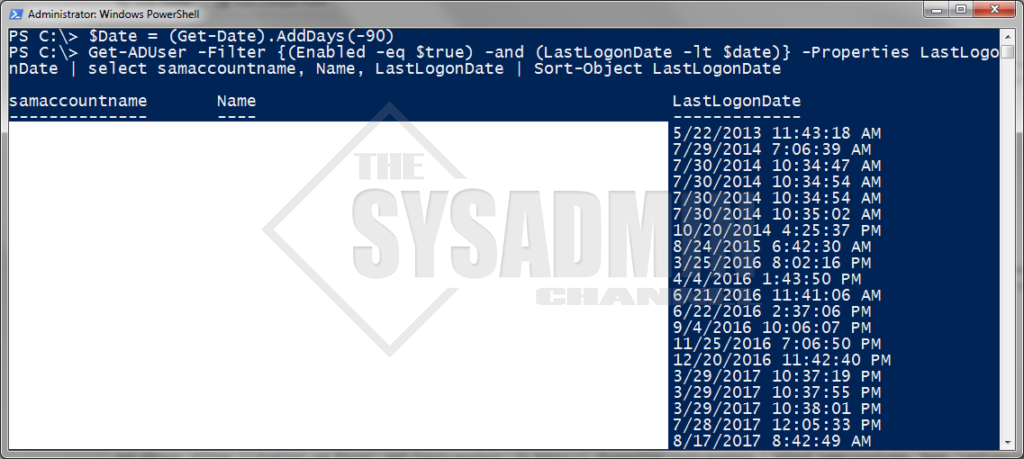
How To Get Last Logon Date for All Users in the Domain
#Getting users who haven't logged in in over 90 days
$Date = (Get-Date).AddDays(-90)
#Filtering All enabled users who haven't logged in.
Get-ADUser -Filter {((Enabled -eq $true) -and (LastLogonDate -lt $date))} -Properties LastLogonDate | select samaccountname, Name, LastLogonDate | Sort-Object LastLogonDate
Hopefully this article helped you figure out which attribute is best to use when you want to Get Last Logon Date for your users. I also hope it gave you an example of why which should be used.
Don’t forget to check our Youtube Channel and subscribe if you want more awesome video content. Somtimes the articles I post don’t have videos and sometimes the videos I post don’t have articles so check us out on the big YT to get awesome sysadmin content all around.


The script is very handy, however you miss one thing.
Users who’ve never logged in, have no LastLogonDate
The -Filter {((Enabled -eq $true) -and (LastLogonDate -lt $date))} misses those users, so they would never show in the list.
That way you can have accounts which are unused for years, as long as they where never used