I have to say Get NTFS Access Permissions and the NTFSSecurity Module is probably one of the best things since sliced bread. Natively, Powershell doesn’t offer a very good solution for checking NTFS permissions so author Raimund Andrée came up with the NTFSSecurity Module to allow for easy security transactions within your environment.
How to Download and Use the NTFSSecurity Module
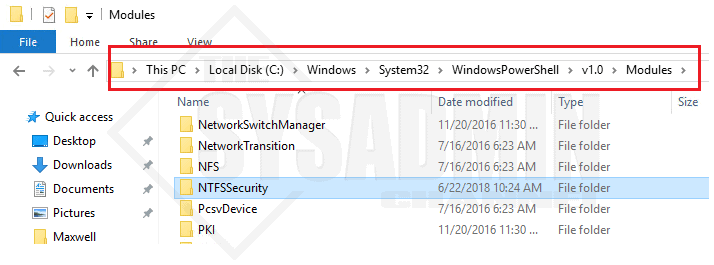
In order to use this incredible and powerful module head on over to the TechNet repository and download the NTFSSecurity Module. Once you have the module downloaded and extracted to a location on your computer:
- Copy the NTFSSecurity folder to C:\Windows\System32\WindowsPowerShell\v1.0\Modules
- Open Powershell and type in the following:
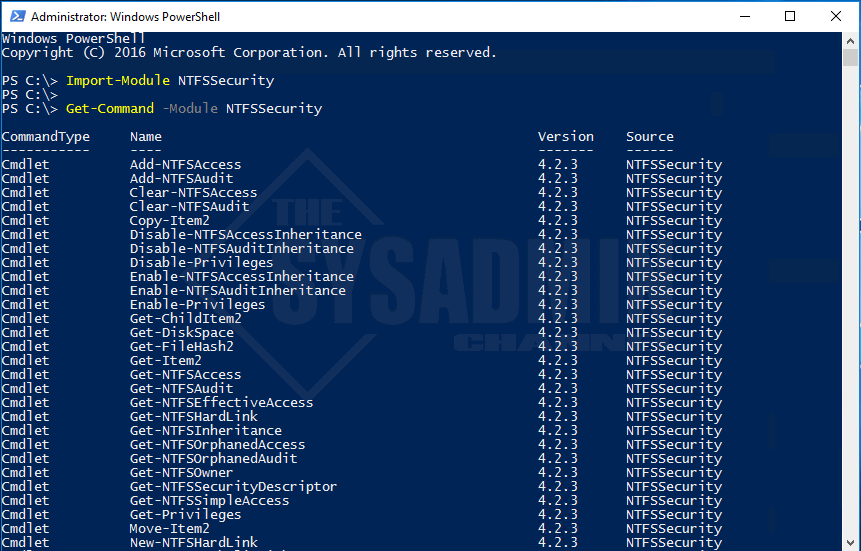
#Importing the NTFSSecurity Module Import-Module NTFSSecurity #Getting all the commands associated with the NTFSSecurity module Get-Command -Module NTFSSecurity
- Check file or folder permissions by doing the following:
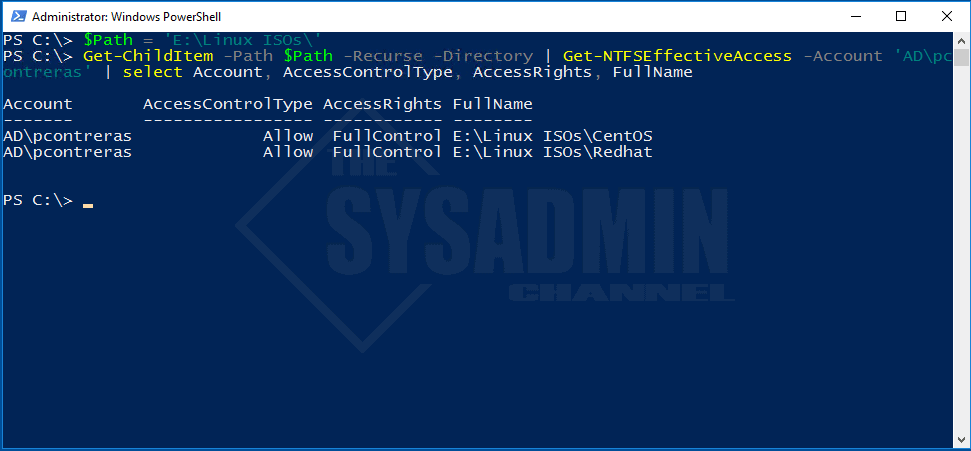
- I like to check effective permissions because it shows if the user has access to a folder even if it’s not explicitly added by the username.
$Path = 'E:\Linux ISOs\' Get-ChildItem -Path $Path -Recurse -Directory | Get-NTFSEffectiveAccess -Account 'AD\pcontreras' | select Account, AccessControlType, AccessRights, FullName
Change Directory Owner Recursively In Powershell
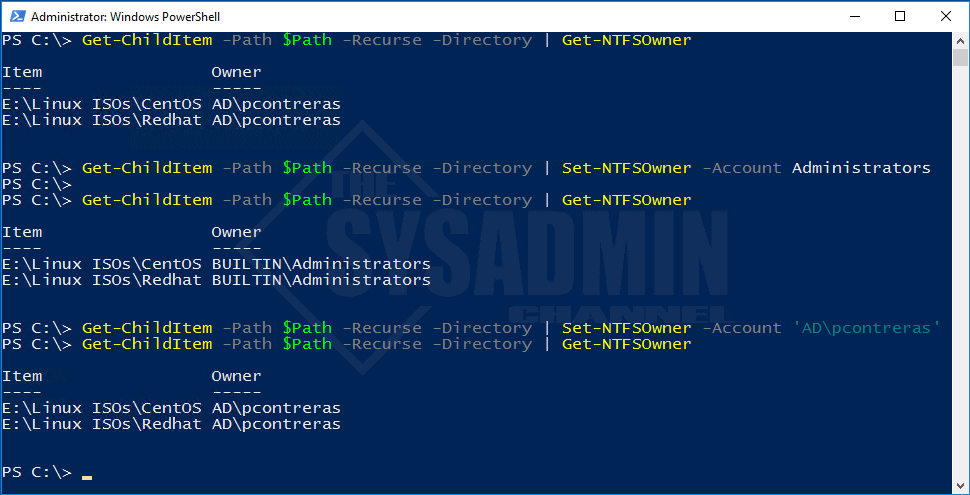
Say the permissions structure was fubar’d beyond belief and we wanted to start fixing it by taking over owner permissions and working our way down the file system. With the Set-NTFSOwner cmdlet we could definitely do that with ease. Here’s how!
$Path = 'E:\Linux ISOs\' #We'll start off by getting current owner permissions to see what's going on. Get-ChildItem -Path $Path -Recurse -Directory | Get-NTFSOwner Item Owner ---- ----- E:\Linux ISOs\CentOS AD\pcontreras E:\Linux ISOs\Redhat AD\pcontreras #Next we'll change the owner permissions to the built-in Administrators of the machine. Get-ChildItem -Path $Path -Recurse -Directory | Set-NTFSOwner -Account Administrators #Checking to see if the new owner permissions were set properly. Get-ChildItem -Path $Path -Recurse -Directory | Get-NTFSOwner Item Owner ---- ----- E:\Linux ISOs\CentOS BUILTIN\Administrators E:\Linux ISOs\Redhat BUILTIN\Administrators #Just for grins we'll set the owner back to pcontreras Get-ChildItem -Path $Path -Recurse -Directory | Set-NTFSOwner -Account 'AD\pcontreras' #Checking once again to see if the permissions were set properly. Get-ChildItem -Path $Path -Recurse -Directory | Get-NTFSOwner Item Owner ---- ----- E:\Linux ISOs\CentOS AD\pcontreras E:\Linux ISOs\Redhat AD\pcontreras
Adding NTFS Permissions to a file or folder using Powershell
$Path = 'E:\Linux ISOs\' #Adding username Djones full control rights to the Linux ISOs folder. Add-NTFSAccess -Path $Path -Account "AD\DJones" -AccessRights FullControl -AccessType Allow -AppliesTo ThisFolderSubfoldersAndFiles
Hopefully this article of how to get NTFS access permissions was useful for you hopefully it saved you a lot of time with regards to permissions. I know it helped save me a ton a time when I had to weed through permissions.
Also, don’t forget to check out our Youtube Channel for more awesome Sysadmin content, especially if you’re more of a visual leaner, you will love what we got going on over there.


Trying to figure out a script that will create an AD group then possibly create a folder on fileshare and set the permissions on an ACL.
How to add ACL for USER2 like has USER1 recursive.
Get-ChildItem c:\TEMP -recurse -Force | where-object {($_.PsIsContainer)} | Get-NTFSAccess –ExcludeInherited -Account AD\USER1
and what next?
I need to add user to in this paths