One of the best recommendations I can suggest to significantly reduce the attack surface for your accounts is to enable multi-factor authentication. To vastly improve the user experience, I would absolutely make the effort to enable Passwordless authentication for Azure AD.
Today we’re going to cover exactly how to enable Passwordless authentication so you can answer the age old question of how to login to Microsoft Authenticator app. To give you a bit of context, when you enable Passwordless, you’re actually using your phone’s authenticator app in lieu of your password along with the biometric (or PIN) that’s set on your device. This allows you to verify your identity by approving the MFA challenge without ever having to enter in your password.
Table Of Contents
Requirements
In order to get passwordless authentication setup and configured in your environment, there are a couple of items that need to be setup beforehand. Don’t worry, we’ll walk through the entire process to ensure you’re at least beta testing this feature. Here’s an overview.
- The user must have Microsoft Authenticator installed on their device
- Microsoft Authenticator must be the default MFA method
- If a user has TOTP as their default method, passwordless authentication will not work
- A device can only be registered to 1 account
- To Confirm Device Registration: Open Authenticator → Settings → Device Registration
- The user will need to be scoped to the authentication method policy
- The app must be a cloud app. Applications hosted in ADFS may not work since it’s a different IdP
Microsoft Authenticator Registration and Management
As mentioned, one of the requirements above is to ensure that the user has MFA push notifications enabled on their account.
If you don’t have admin access to check these settings, they can check themselves by doing the following:
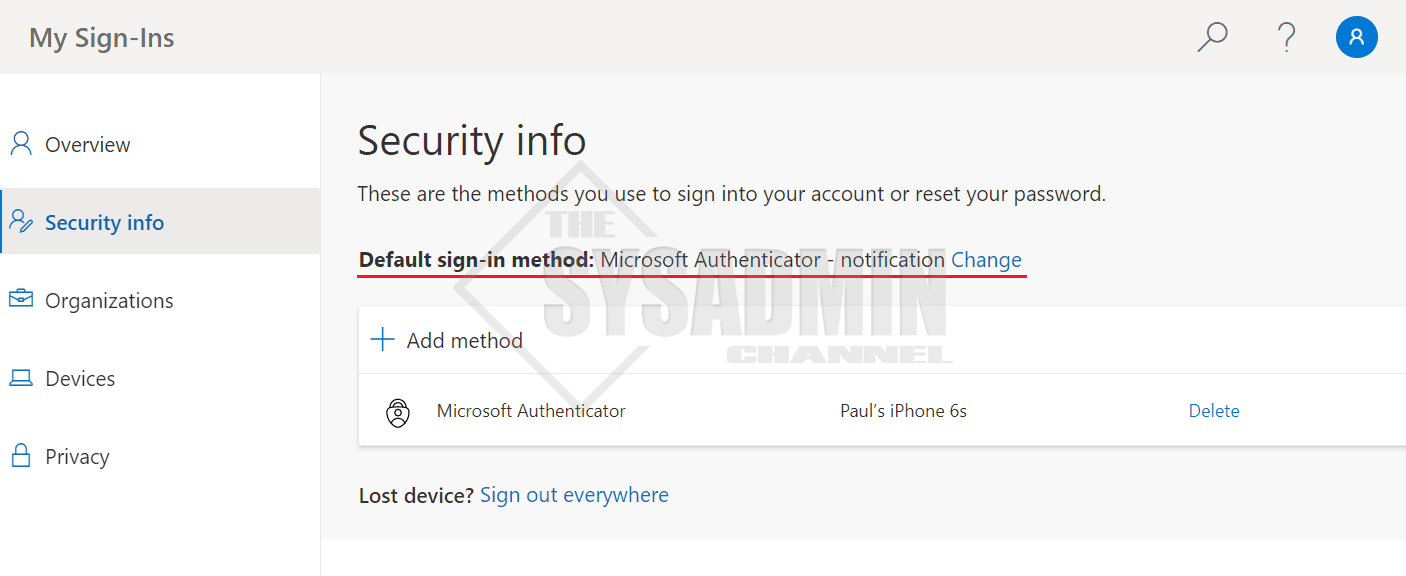
- Navigate to https://aka.ms/mysecurityinfo
- In the Security info blade…
- Ensure the default sign-in method is set to Microsoft Authenticator – notification
- If it’s set to TOTP, you might need to click Add method and register a push notification method
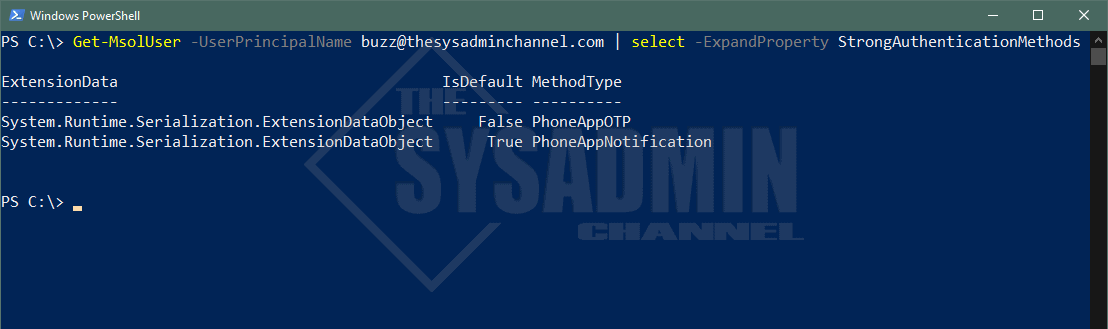
If you are an admin and you’re rolling this out to a larger set of people, it would be a good idea to get ahead of the curve and find out the user’s default strong authentication method. Luckily, we have the ability to check this using the MSOnline Powershell module.
As of today, we’re able to get Azure AD authentication methods using Microsoft Graph API, however Graph API does not have the capability to view the default method so we’ll need to rely on the MSOL module.
How To Enable Passwordless Authentication Azure AD
Now that we’ve met the requirements and confirmed that MFA push notifications is the user’s default method, we’re now read to move forward with setting up passwordless for your org.
Configure Administrative Settings for Passwordless Authentication
Let’s follow the steps below:
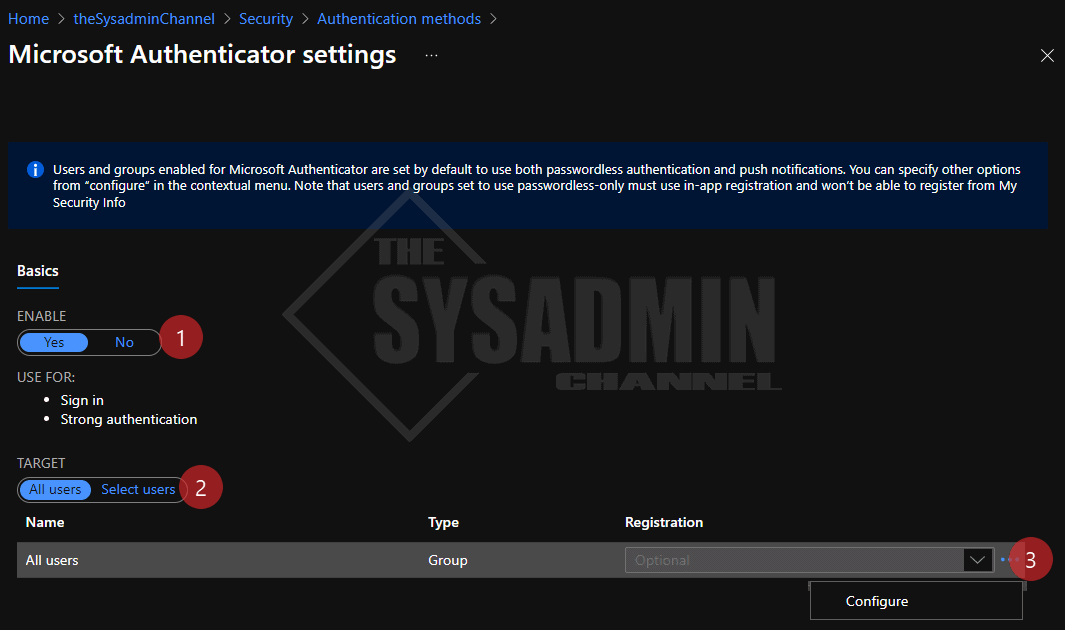
- Navigate to the Azure Active Directory -> Security -> Authentication Methods -> Microsoft Authenticator
- Set the policy to Enable
- Set the target to All Users or specify a pilot user/group
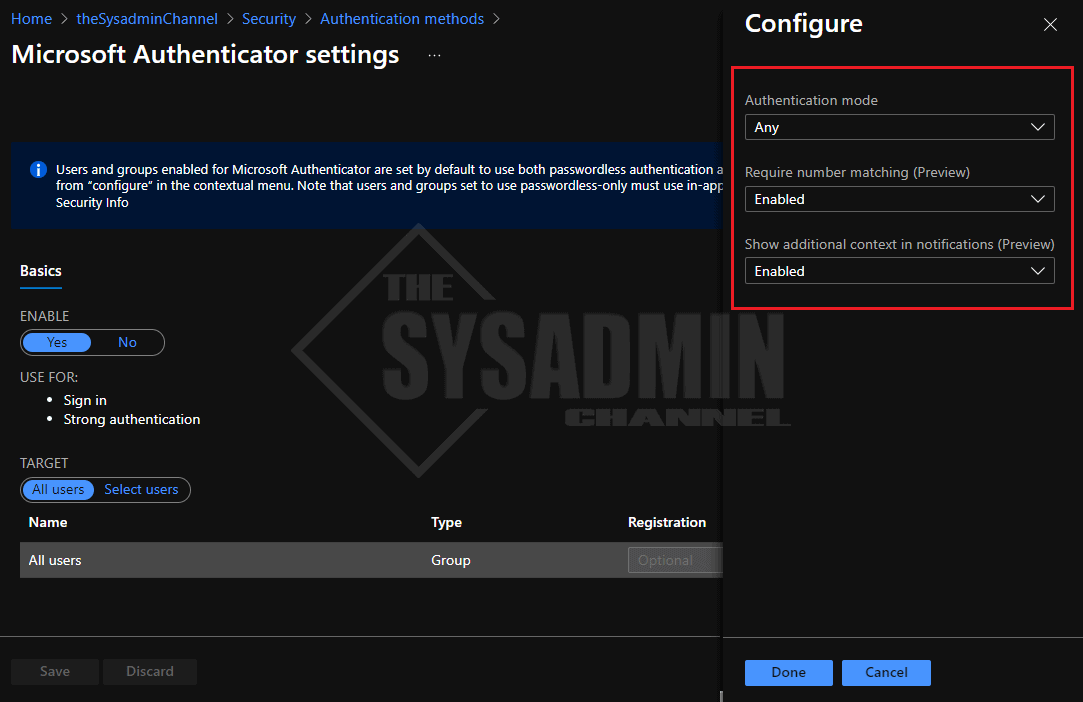
- As a bonus, enable location rich context For MFA Push Notifications and number matching for icing on the cake
Client Setup and User Experience
Assuming the user is in scope of the policy, let’s review the setup that’s needed as the end-user. It is relatively straight forward and setup is only needed once per device.
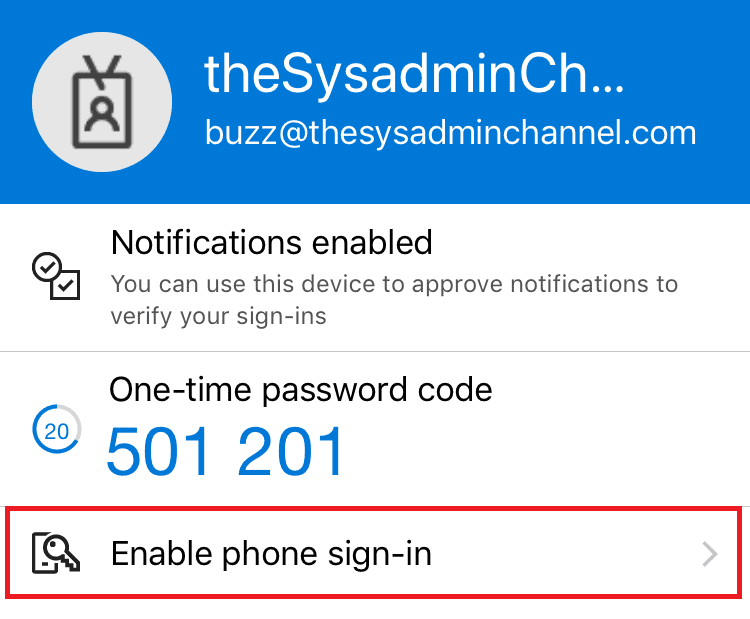
- On the user’s mobile device, click the entry for the account
- Click Enable phone sign-in
- Select continue on the next screen and you’ll be prompted to authenticate to approve MFA
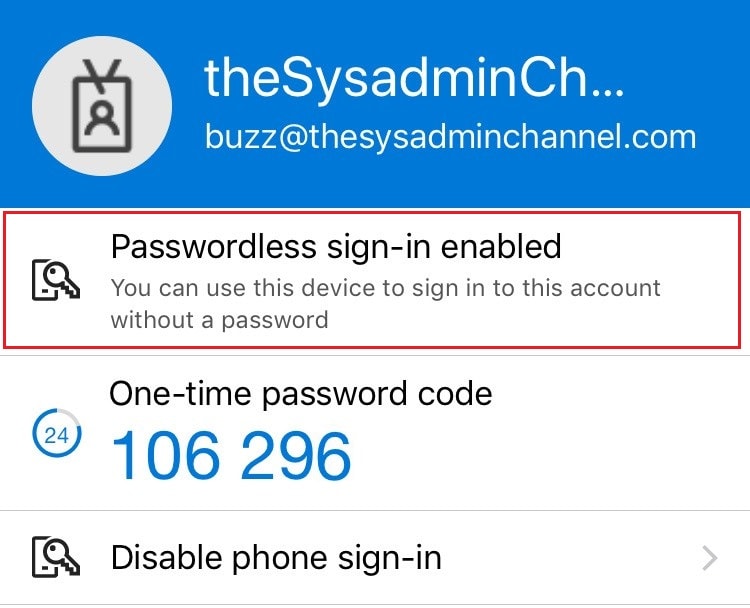
- If successful, click back into your account and you should see Passwordless enabled
Now that we’ve enabled passwordless on the client device, let’s activate it.
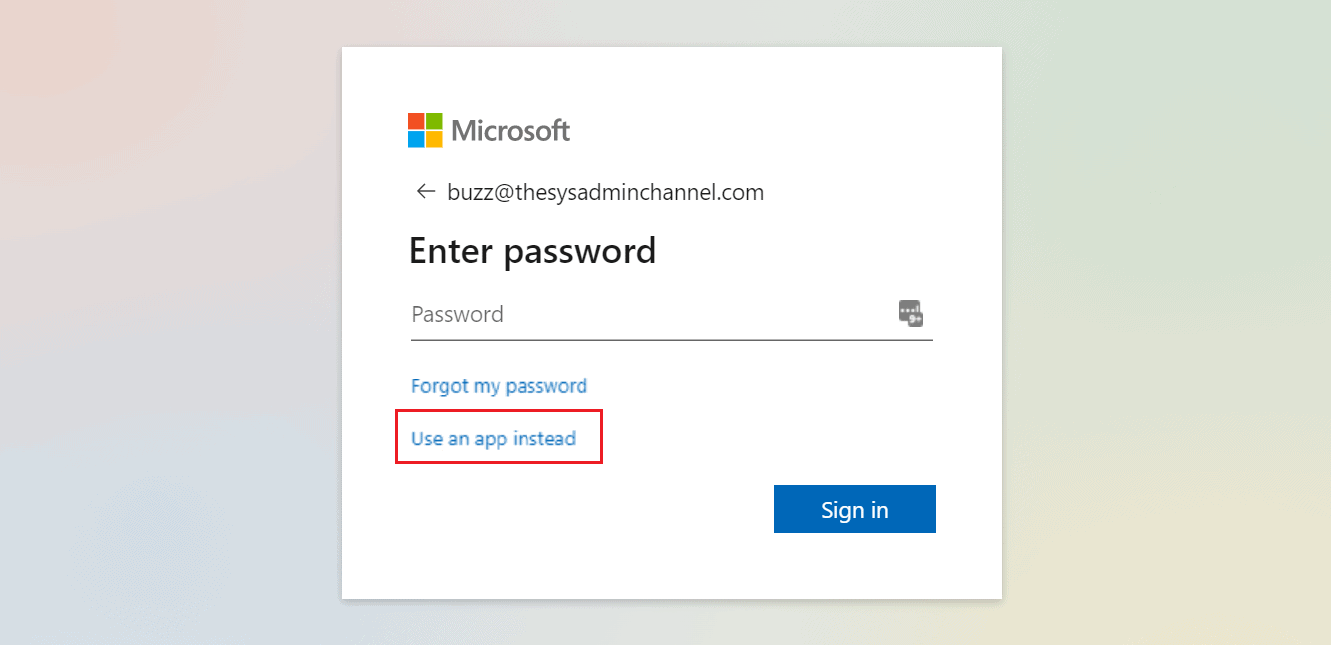
- Open an incognito browser and enter in your user name
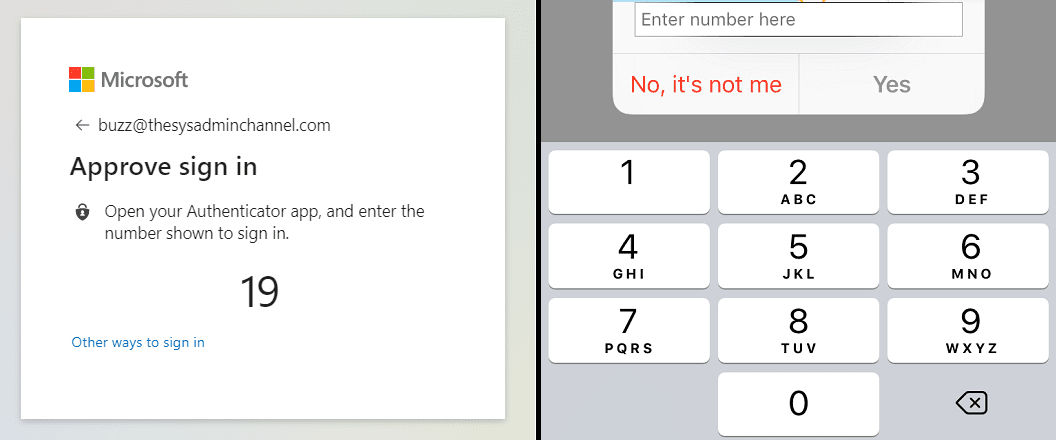
- On the prompt to enter your password, select Use an app instead (or other ways to sign-in if Fido2 is enabled)
- Enter the corresponding number
Conclusion
That’s it! Passwordless is now enabled on your account. Going forward, anytime you try to authenticate to a cloud resource you will be able to use passwordless authentication. One caveat to this is, if the application is hosted in your onprem ADFS, your mileage may vary.
All in all, I think this one of the great features that you should have rolled out to your organization. It is user friendly, adds security with MFA and is good practice to implement.