Whether you’re focusing on internal or external users, having 2-factor enabled so people can access resources in your org is always a recommended practice to enhance your security footprint. Today, we’re going to focus our efforts using conditional access to enable MFA for external users Office 365.
Table Of Contents
Requirements
In order to move forward with enabling multi-factor authentication for guest users there are a couple of requirements that are needed. Let’s list them out here so we have a clear understanding of what they are.
- Azure AD Premium license (P1 or P2)
- A valid external email account that you can add as B2B guest user
In my lab tenant, I have EMS-E5 licenses which is P2 so I’m good to use conditional access policies to get this all setup.
End User Experience and What to Expect
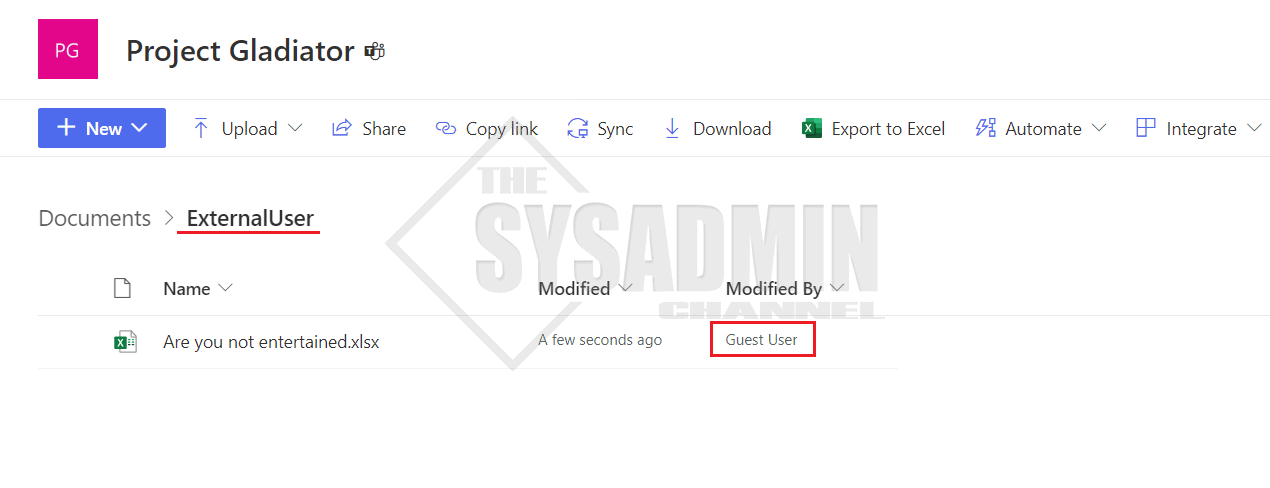
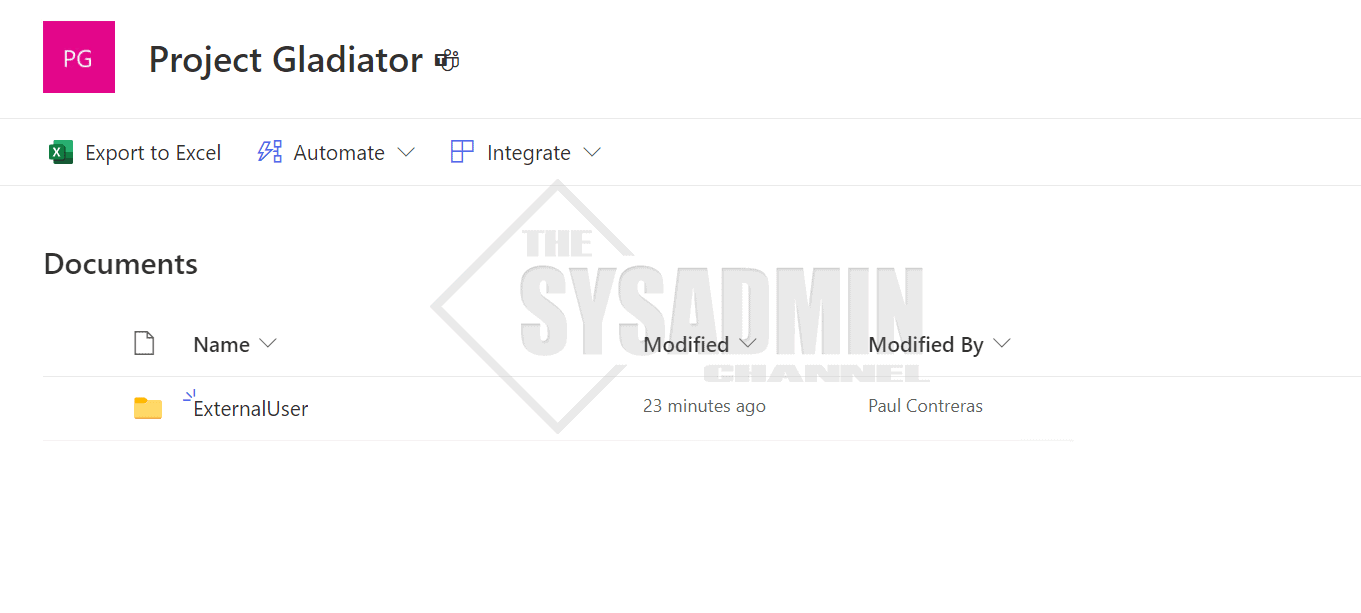
To give you some context on how I’m testing this in my lab tenant, I’ve granted the external user who is named “Guest User” access to a SharePoint site that I’ve created for this purpose.
The SPO site, Project Gladiator, has an “ExternalUser” folder that I’ve setup to mimic a real-world scenario. This folder is where people from other orgs will update their notes to use for collaboration.
At this point, I’ve sent an invitation to the guest user and they have accepted the invite. Next, I copied the link to that folder and sent over to the external user so they can access the resources that are setup at their convenience.
For now, we’ll take a moment to check in on the user experience before and after the policy is enabled.
What to Expect if the User has MFA Enabled
Let’s take a moment to clear the air first. If a user has MFA enabled on their own home tenant, this doesn’t mean that they’ll be prompted to confirm their identity with an MFA prompt on your resource tenant. There are now ways to trust the MFA claims from the home tenant using Cross Tenant Access Policies (xtap) but that’s a little outside the scope of the this article.
It will actually take some effort to enable MFA on a resource tenant if you’re not enforcing it so chances are they won’t do unless you make them.
However, if a user has enrolled in MFA in the resource tenant, then they’ll continue to be prompted for MFA as they previously have.
What to Expect if MFA is not enabled for the User
Since there aren’t any policies that are enforcing MFA for external (guest, B2B etc..) users, this user is able to get in with just a username and password. If someone potentially compromised the remote credentials, they now have access to your tenant. This is obviously a no-no and is the reason why enabling MFA is so vital to security.
We haven’t touched on how to enable the policy yet, however, what can we expect when we enable MFA for external users Office 365 / Azure AD?
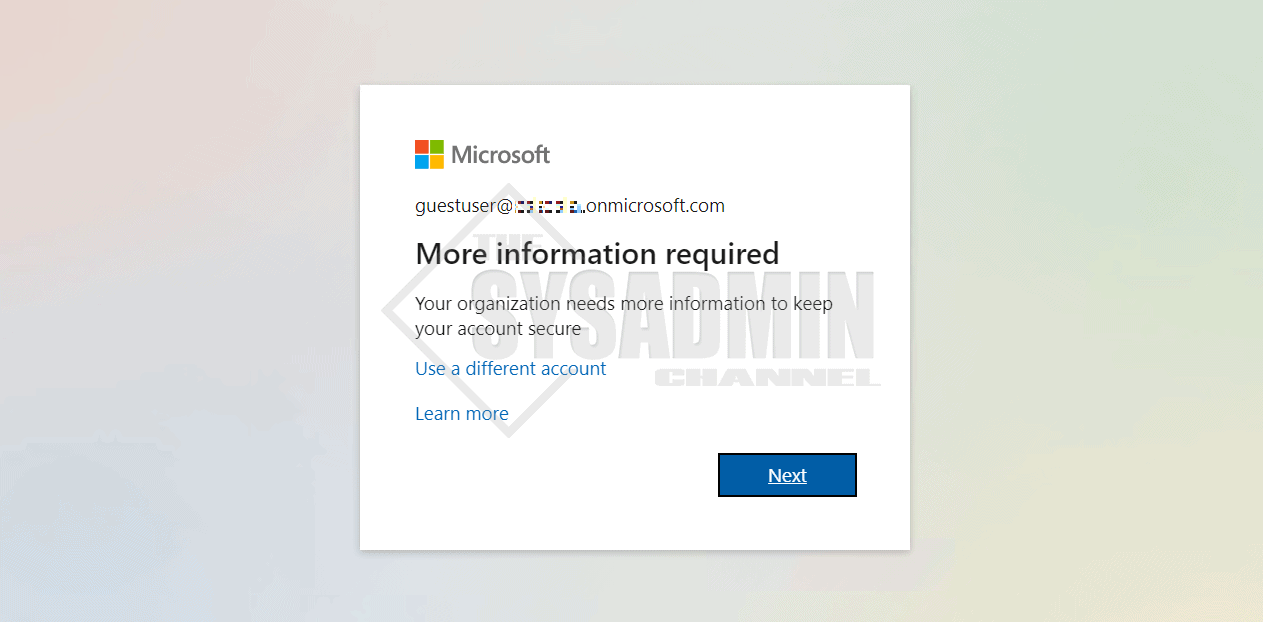
Once you enable the policy, the user would be shown the typical prompt for when a user tries to enroll in MFA in the home tenant.
How To Enable MFA for External Users Office 365
Now that we know what it looks like, next up is to use a conditional access policy template in Azure AD to set it up. As mentioned, this would require you have a premium license so hopefully you have that setup in you tenant so you can follow along. Let’s review the steps needed to enable this policy.
In Azure AD:
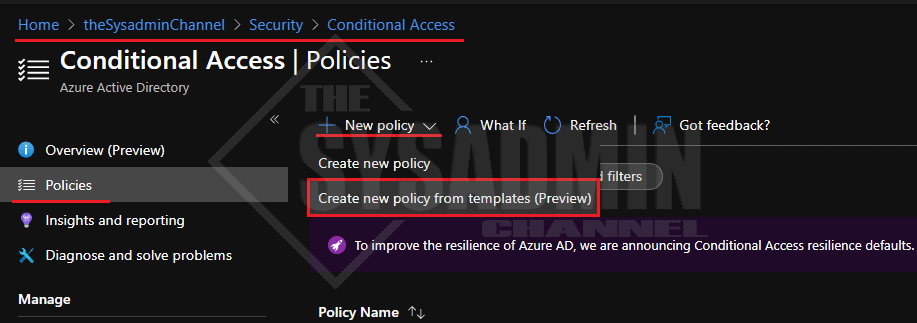
- Navigate to Security -> Conditional access -> Policies
- Click New Policy -> Create new policies from templates
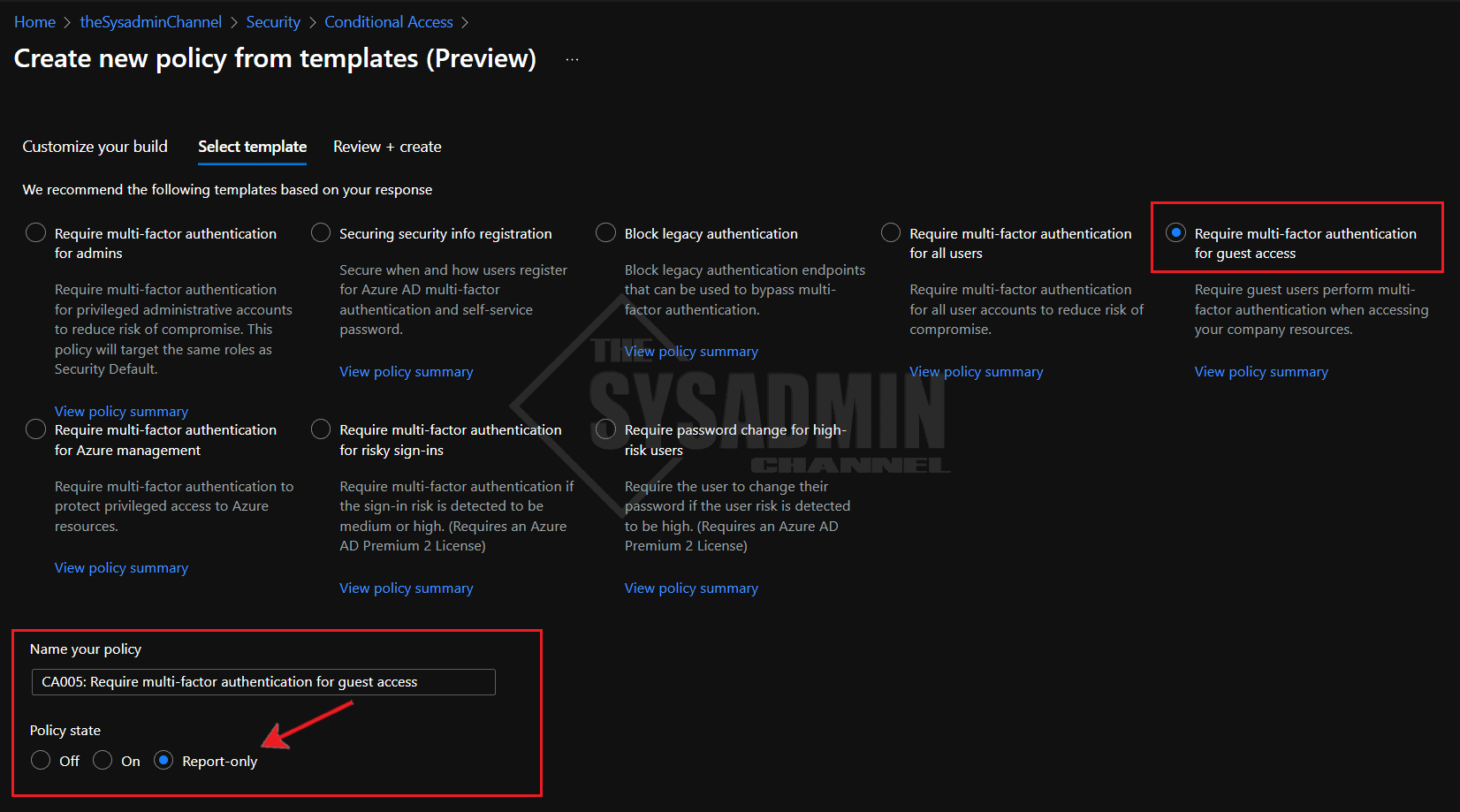
- Under Customize your build: select Identities and click Next
- select Require multi-factor authentication for guest access and click Next
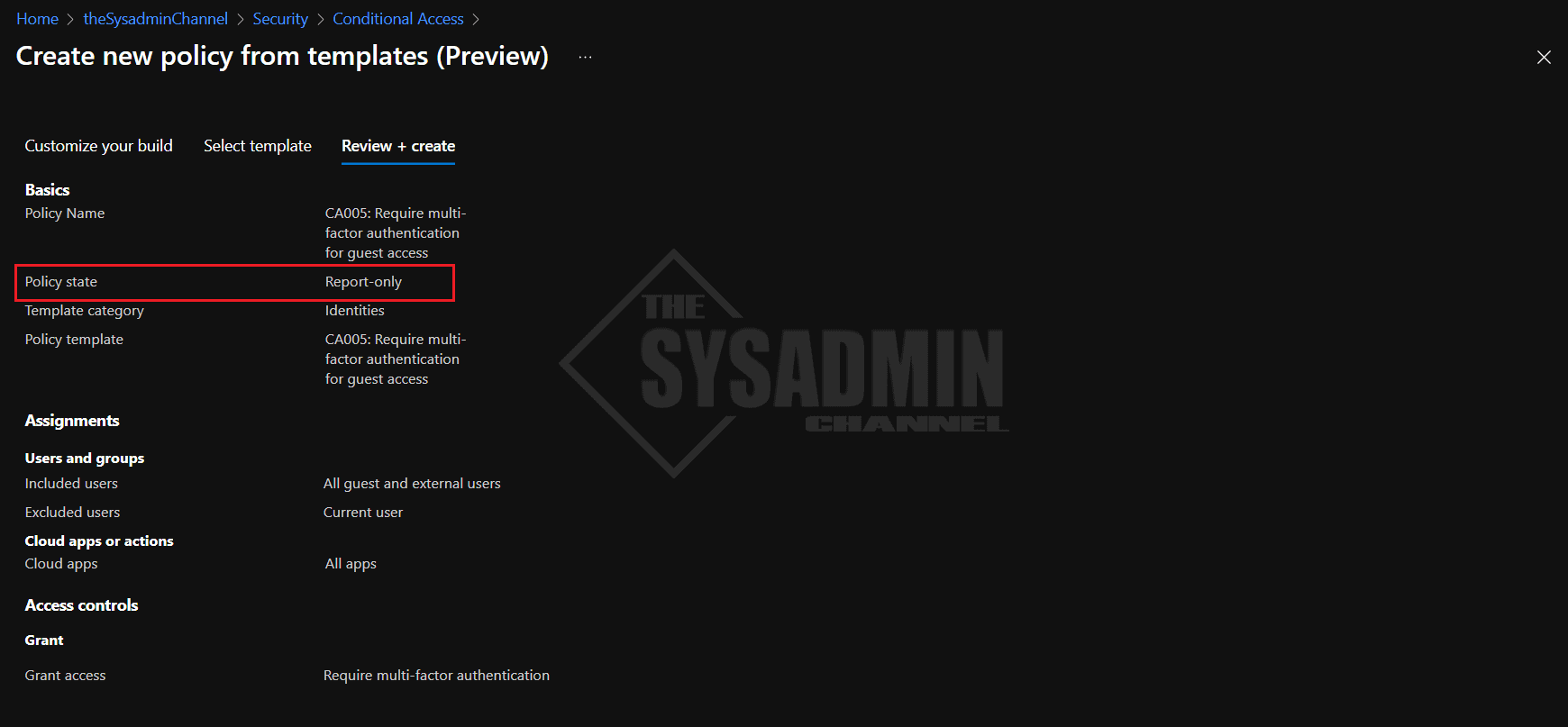
- Review the policy and confirm it is in Report-only
- Click Create Policy
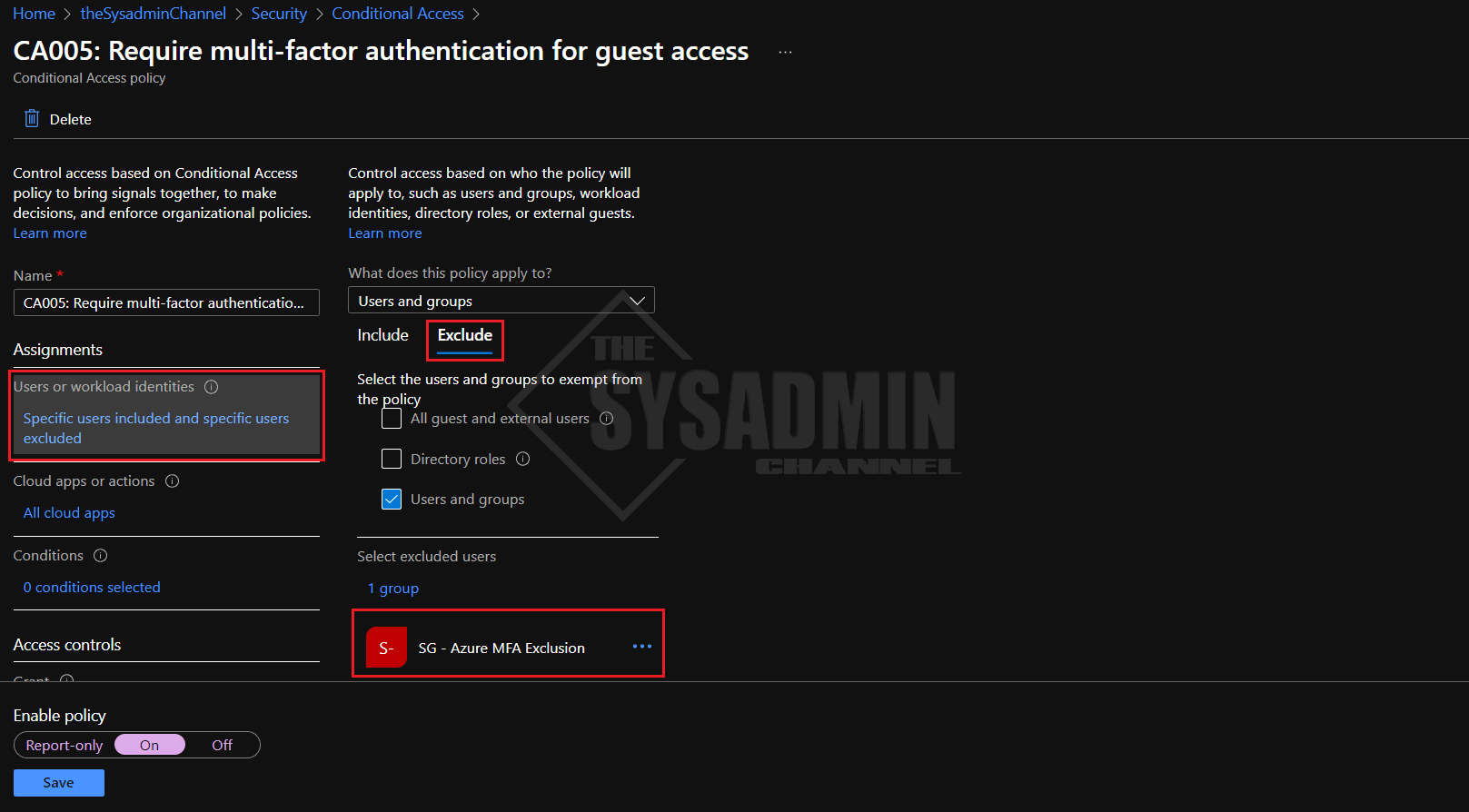
Now let’s go back into the policy and under Assignments -> Exclude: Enter the breakglass account and an MFA exclusions group in your own tenant. Hopefully this won’t be needed, but if someone decides to modify the policy and applies it to people in your org, you’ll at least have some specific exclusions in place.
Finally, enable the policy and click save. External users will now need to enable MFA to access resources in your home tenant.
Conclusion
Hopefully this article showed you how to enable MFA for external users Office 365 and was easy to follow along. If you haven’t done so already, be sure to enable MFA for your regular users to ensure you’re covered across the board.


I have MFA already enabled and we have selected all users. Will this by default apply to guest and externals users? I want to make sure because everything I have read talks about assigning MFA to specific groups, where we went and applied it to all users.
This should also apply to guests as well as long as you didn’t exclude guest users in your options.