What Is A Break Glass Account and Why You Need It
A break glass account is an account that is used for emergency purposes to gain access to a system or service that is not accessible under normal controls. You, as a systems administrator should not only document all of your break glass accounts but regularly audit those accounts to ensure that the correct people have access.
More importantly, the reason you need a break glass account is to bypass the controls put in place that are there to increase security.
Table Of Contents
What Roles Should Break Glass Accounts Have?
Typically any account that is used for emergency purposes needs to have the rights to be able to gain access to the system and revert any controls or lockouts that are in place. Nine times out of ten, I would recommend that the account have administrator rights to ensure you’re up and running as soon as possible. Furthermore, a break glass account is usually highly privileged and has the least amount of controls in place so it needs to be secured in a vault that very few people have access to.
How Many Emergency Accounts Should I Have?
Ideally you would want 1-2 emergency account per platform. Let’s take Microsoft’s Azure Active Directory for example. Although you can have many administrators or Global Admins, Microsoft recommends 2 break glass accounts for the M365 platform. The reason being is that you’ll want a backup to the backup just for good measure.
Lets say you deploy Multifactor Authentication and your policy is scoped to all users, you’ll want to have this break glass account excluded from that policy to ensure that you can still login if admins aren’t able to get in.
In this scenario, the Azure AD account would have Global Admin rights, it would be excluded from the MFA policy and finally, it would NOT be an on-premises account. Specifically, this Global Admin account should be an onmicrosoft.com account in the event your on-prem AD has issues.
How To Monitor Break Glass Accounts Sign-in And Audit Logs
Every platform is different so it will be nearly impossible to give an answer to anything really specific. However, if we use our example of Azure Active Directory (Azure AD), I can give you a general idea of what this would look like in a real world example. If you’re already using Azure AD that’s great! If you’re not, but you plan to migrate sooner than later we got you covered in our Exchange Migration YouTube Playlist.
As I mentioned, it is recommended that you monitor sign-in and audit log activity from emergency accounts. I would also highly recommend you trigger a notification to your administrators when there has been activity. How do I do this you ask? Here is a quick break down of what that looks like.
- Import or Install AzureAD Module
- The cmdlet Get-AzureADAuditSignInLogs can quickly gather those logs using Powershell
- The cmdlet Send-MailMessage can send an email to send you a notification, also using Powershell
- Setup a scheduled task to check on a regular basis
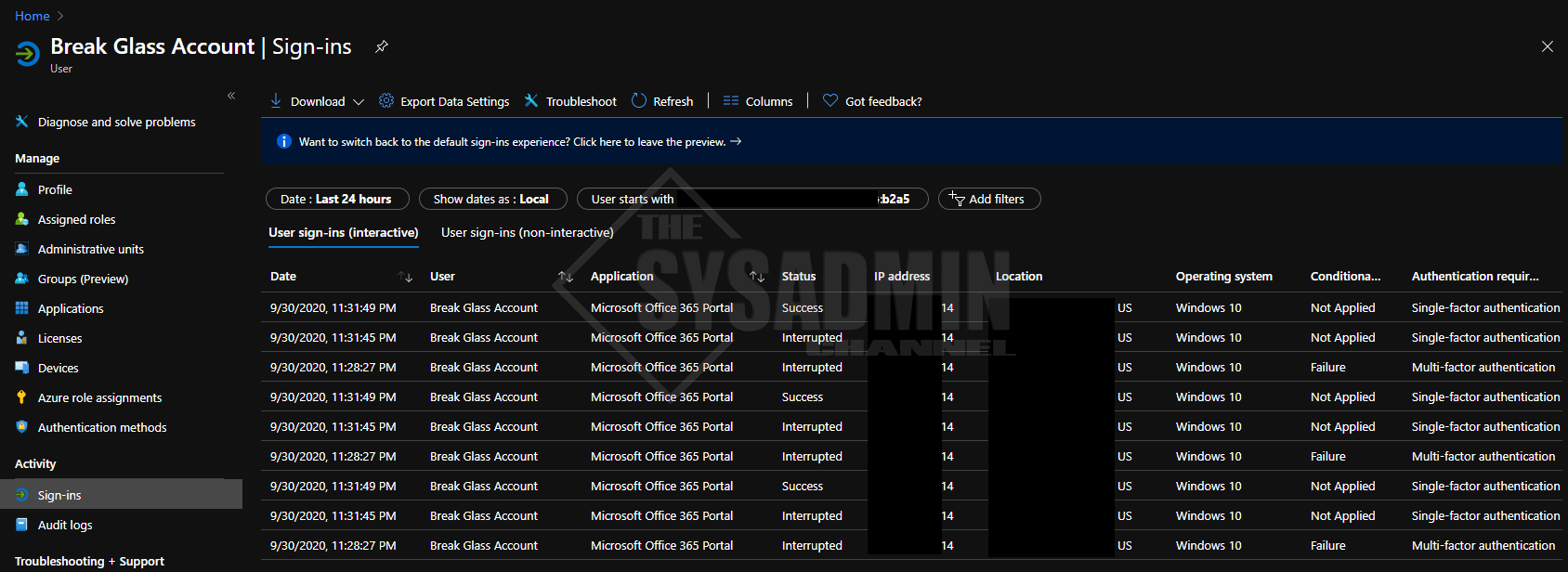
Get-AzureADAuditSignInLogs Example
Here is a quick example of what Get-AzureADAuditSignInLogs would look like.
#Connect to Azure Active Directory Import-Module AzureAD Connect-AzureAD -AccountId [email protected] #Get Date and then check for sign-ins after said date $Date = (Get-Date).AddDays(-1).ToString("yyyy-MM-dd") Get-AzureADAuditSignInLogs -Filter "UserPrincipalName eq '[email protected]' AND CreatedDateTime gt $Date"
This short script block above will show the same information you’re used to seeing in the GUI.
Conclusion
At the end of the day you’ll need to ensure you have a backdoor to get into your platform and a break glass account is a perfect use case for it. I hope this article was informative for you and if there’s one take away from this article, that is… Subscribe to my Youtube Channel. Because why not. 🙂

